This post is part of a multi-part series defining maturity model levels for endpoint devices. Today we will be covering Endpoint Security Level 5....


This post is part of a multi-part series defining maturity model levels for endpoint devices. Today we will be covering Endpoint Security Level 5....
Introduction To The Series You have enrolled your endpoints into Microsoft Intune, you’ve configured policies, and you are managing your devices....
![[Case Study] Helping One Global Private Equity IT Department Stay Lean, Unseen, and Focused](https://b2186977.smushcdn.com/2186977/wp-content/uploads/2021/12/Featured-Image-Template-2.jpg?lossy=0&strip=0&webp=1)
In endpoint management, the less you're noticed by end users, the better that you're doing at your job. And when you're a global Private Equity firm...

Inefficient app deployment is one of the big causes of resource waste (and endpoint security holes) that we address here at Model Technology...
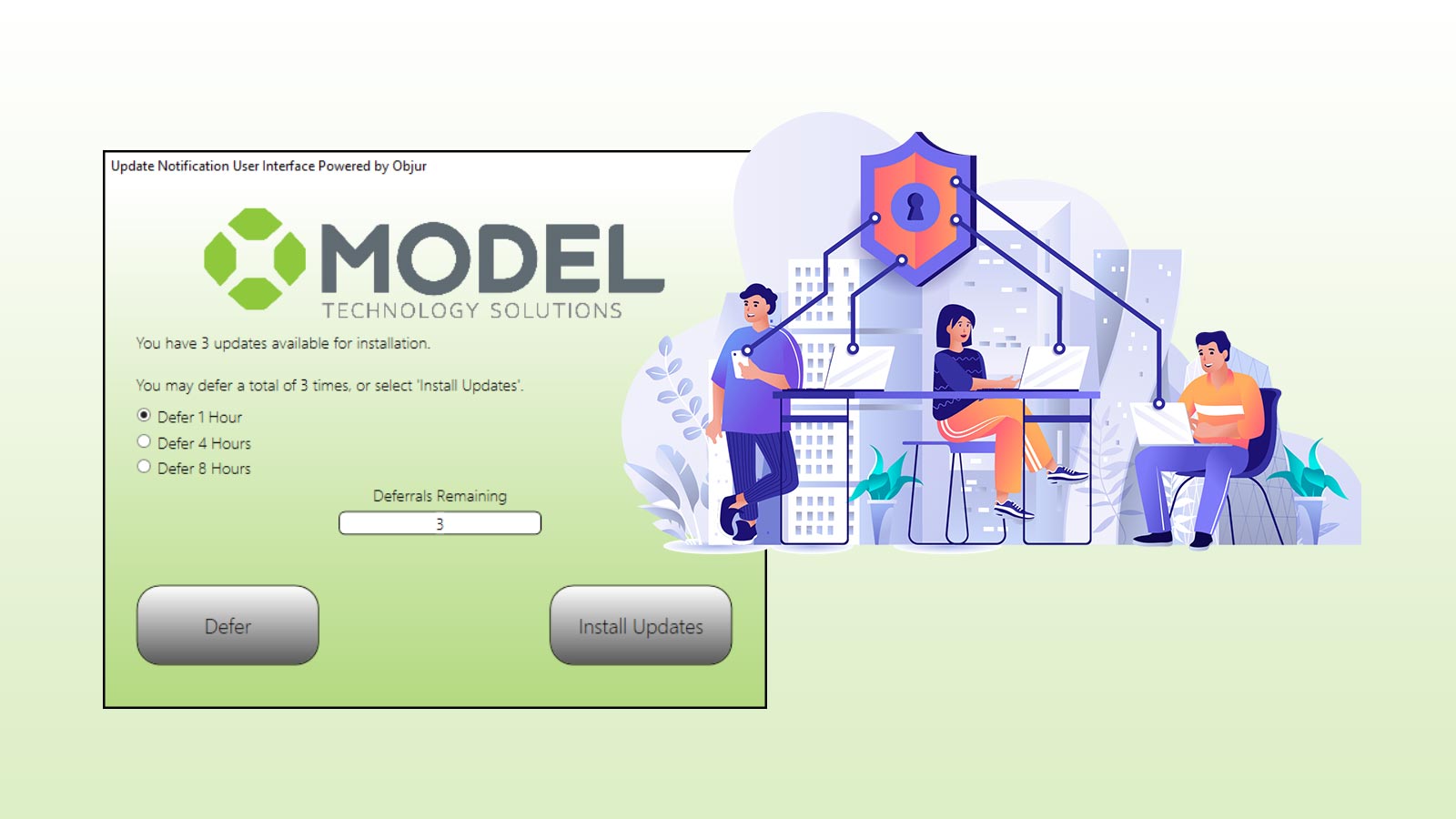
It's all about the boot, not just the patch. Endpoint patching only increases security when the end user reboots and applies the update to their...
In healthcare IT, the management of devices and applications is paramount, more so today as IT...
In the rapidly evolving world of healthcare IT, Directors and Managers are increasingly confronted...
In the ever-evolving landscape of healthcare IT, the surge in cyber threats, particularly phishing...
Prove you’re cyber-ready and reduce your premiums through our NIST-based cybersecurity assessment. Then make the most of your assessment results through monthly consulting sessions with our vCISO Director of Cybersecurity.