Since Microsoft Intune’s debut in 2011, it has become a market leader within the UEM category. A simple user interface and its ever-changing and feature-rich capabilities has made managing devices plain sailing – for the most part. Two of those helpful features are:
- The management of device compliance
- Conditional Access
Though these are two different features inside of Microsoft Intune, they are often used cooperatively to manage endpoints and improve endpoint security. This blog serves as an introduction into these capabilities.
What is Device Compliance and Conditional Access?
So, what is Device Compliance and Conditional Access? Let’s look at them in terms of health.
- Compliance: Tells you if your device is healthy or not.
- Conditional Access: Determines what to do with these devices depending on their health status.
The purpose of these two features is to limit access of devices that do not meet your baseline of configuration and keep them from creating vulnerabilities in your infrastructure.
Finding Pre-Configuration Settings in Intune
If you navigate within Intune to Devices | Policy | Compliance Polices you will see some pre-configurations for these settings.
These settings help you manage:
- The status of devices with no compliance assigned
- Compliance status validity period
- Noncompliant devices
- Notification to those devices
Creating New Policies in Intune
To create a new policy, navigate to Devices | Policy | Compliance Polices and click “+ Create Policy”.
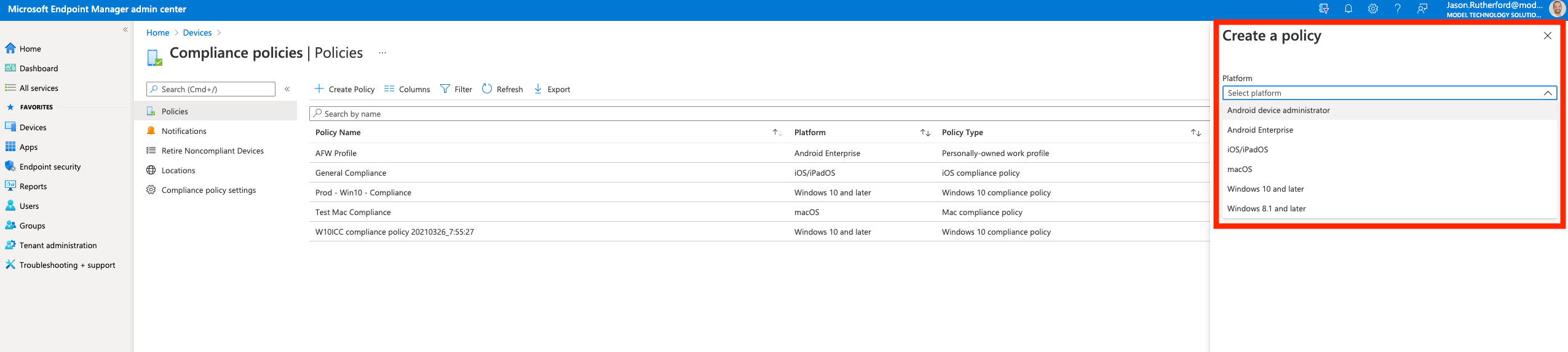
There you will select the platform and the compliancy type.
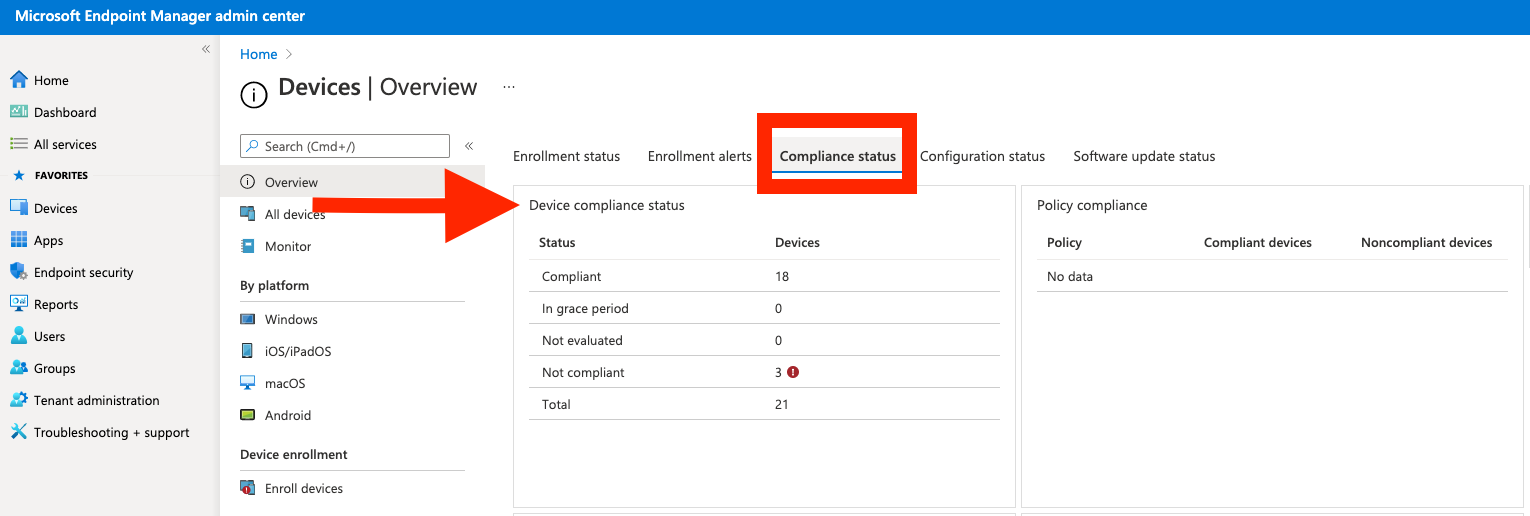
What you want to do is to paint the ideal picture of health for your device. You should also be able to monitor your device’s compliance status by navigating to Devices | Overview and selecting the “Compliance Status” tab.
Setting Conditional Access Settings in Intune
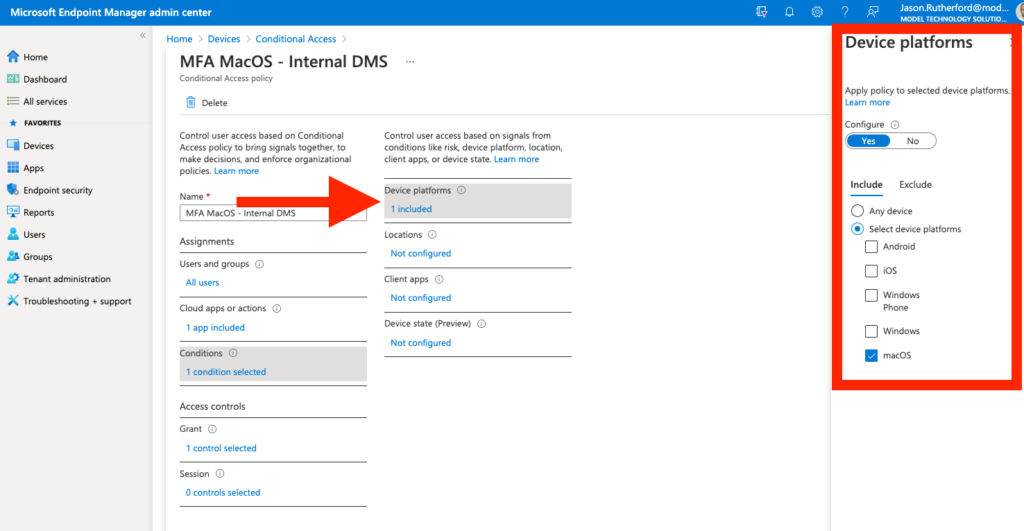
You can reach your conditional access settings by navigating to Devices | Policy | Conditional Access. Here you will then be able to set your conditional access policies. You will be able to create new policies, modify the properties of existing policies for tasks such as choosing what users or groups to include/exclude from policies and set those conditions for your devices that are/are not compliant.
There are many facets to the conditions for conditional access, we’ll cover those in a later blog more. But as a basic example, targeting a group of users (in our case for this example “all users”), accessing a specific application (in our example an on-premise web-based document management system) as seen below:

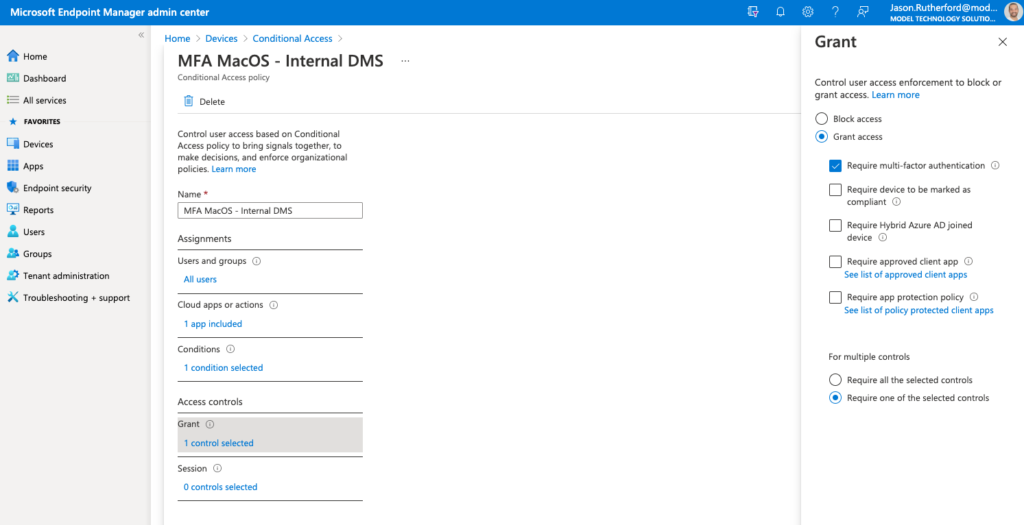
Stay tuned for more conditional access and compliance blogs!
