Looking to do 2012 R2 DirecAccess? You only want a single nic? And you want to use a NAT? Well read on then!
Recently we implemented DirectAccess for our internal infrastructure. A couple of items to note is that I’m not publishing the final configuration that’s been updated with the proper certificates, but the information posted will get you a working DirectAccess with a single NIC behind a NAT infrastructure.
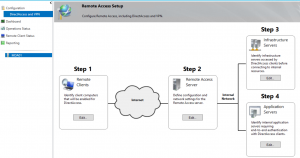
There are several ways to setup DirectAccess, this document is the initial configuration for Model Technology Solutions. Additional Considerations include:
- PKI
- CRL/CDP configurations for internal and external clients
- Not using self-signed certificates
- NRTP
- Additional exclusions
- NLS
- Additional URLS
- Load balancing DirectAccess Servers
- Additional transition technologies
Domain Controller Configuration
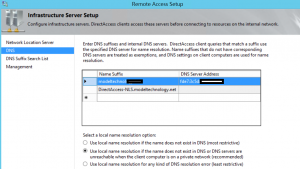
DNS Configuration
- On a domain controller (DNS Server) run this command:
dnscmd /config /globalqueryblocklist wpad
Disable ISATAP
- If you’re using a single NIC behind a NAT for the DirectAccess server you’ll be using IP-HTTPS and you will need to disable ISATAP on the Domain Controller by running this command:
netsh int ipv6 isatap set state disabled
Group Membership
- Create an Active Directory group which computers will be placed into to enable DirectAccess
DOMAIN\Da-Computers-GROUPNAME
Additional Notes
- The IPV6 Address will be handled automatically
- Ensure the DNS server is listening on the IPV6 Address (properties of the DNS server, interfaces tab)
- Four DNS records will be created as part of the DirectAccess Setup
- The Domain Controller does not need the Firewall enabled
Public DNS Record
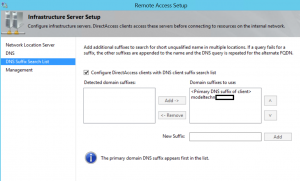
- Create a public DNS record for the DirectAccess URL. If you’re using a different external domain namespace than your internal domain namespace you won’t have to add the DirectAccess URL to the NRPT exclusions. If they are the same, you’ll need to add the URL to the NRPT exclusions in Group Policy.
something.model-technology.com points to the external IP of Model’s Cisco ASA (83.25.50.20) – (This isn’t the real IP :))
Firewall Configuration
Access Rule
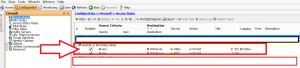
- an access rule from Any source to the DA Server (192.168.20.13) using port 443 needs to be created
NAT Rule
- a NAT rule needs to be create for the bi-directional communication over 443
DirectAccess Server Configuration
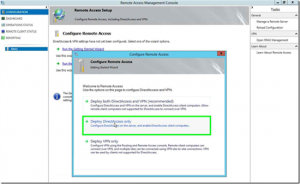
- From the features section in Server Manager, choose Remote Access
- Once the base installation is complete, a post configuration will need to be completed
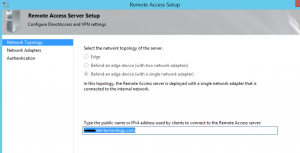
- Choose “Deploy DirectAccess Only”
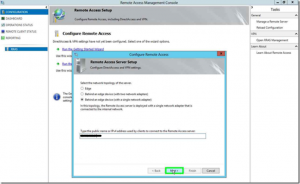
Next type in the DNS name for Model’s configuration, we used da.model-technology.com (not shown in the screenshot)
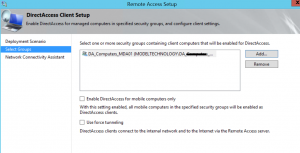
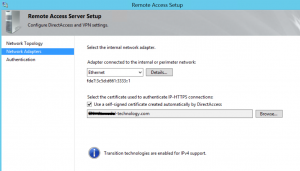
On the next screen, choose the “EDIT” hyperlink before clicking next, so you can configure the group for the DirectAccess clients properly
Note: There’s a missing screenshot to configure the group, but this step is critical! You’ll figure it out once you see the options.
- Click Ok, then Finish…
Disable ISATAP
- If you’re using a single NIC behind a NAT for the DirectAccess server you’ll be using IP-HTTPS and you will need to disable ISATAP on the DirectAccess Server by running this command:
netsh int ipv6 isatap set state disabled
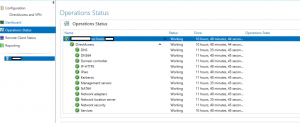
Verify DirectAccess Configuration
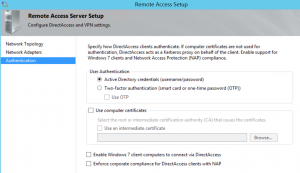
Please note that Model’s configuration is not utilizing a PKI infrastructure, but rather self-signed certificates…
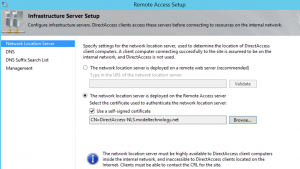
Note, the DNS server address is the IPV6 address of the DirectAccess Server, not the Domain Controller
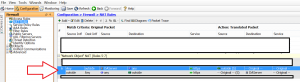
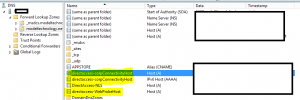
Verify DNS Configuration
Note these are configured automatically during the DirectAccess setup.
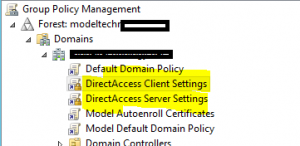
Verify Group Policy Configuration
Note, these policies are created automatically. Because we have blocked inheritance enabled on certain OU’s, I have set them to be enforced.
Additional Notes
- The IPV6 Address will be handled automatically
- The DirectAccess server needs to have the firewall enabled to function. If you have a group policy turning off the firewall on servers, the DirectAccess Server will need to be excluded from the policy.
- WinRM cannot be configured through Group Policy on the DirectAccess server. If you have a group policy in place, the DirectAccess Server will need to be excluded from the policy.
- There are several hotfixes pertaining to the DirectAccess server and DirectAccess clients, if you see the references section.
DirectAccess Client Configuration
Note, there are Operating System dependencies for DirectAccess clients, please look them up to ensure you have the correct version of the Operating System.
- Once the client is a member of the DirectAccess group, is in an OU where the Group Policy will be applied, and the computer has been rebooted, you should see the new DirectAccess Icon in the Network Configuration screen
- Once you move to an external network, the DirectAccess connection should move to a connected state.
Troubleshooting
There’s a utility from Microsoft that will test the various aspects of the DirectAccess infrastructure from the client side called the DirectAccess client troubleshooter. It’s a free download from Microsoft and is useful for identify the issues with DirectAccess and can be found here DirectAccess Troubleshooter
References
- http://www.syscomlab.blog.com/2012/09/directaccess-for-windows-server-2012-guide/
- http://directaccessguide.com/2013/10/07/setting-up-single-nic-directaccess-servers-with-an-external-load-balancer/
- http://support.microsoft.com/kb/2883952
- http://www.dickson.me.uk/2012/03/20/ipv6-disabling-isatap-and-6to4-in-windows-7/
- http://technet.microsoft.com/en-us/library/jj574174.aspx
- http://blogs.technet.com/b/canitpro/archive/2014/01/06/step-by-step-enabling-directaccess-in-windows-server-2012.aspx