Welcome to session number three in our multi-part series on Unified Endpoint Management! In this session, we’ll:
- Recap what Unified Endpoint Management means
- Review our maturity model phases and the categories associated to it
- Take a little bit deeper look at the Management Infrastructure Level 2
- Cover a high level review of what that means to be a Level 2 Management Infrastructure
- Explore some general next steps of where to go from there
- Talk about some actionable steps that you can take for more information
What Is Unified Endpoint Management?
Generally speaking, Unified Endpoint Management is a single platform for management of devices such as phones, tablets, laptops, and desktops.
Standard Definition: A single platform for management of devices such as phones, tablets, laptops, and desktops supporting many different use cases.
Model has just a little bit of a different approach. We also look at the processes that are required to support the management of those devices in addition to just the platform itself that’s managing them.
Model’s Definition: A collection of processes supported by technology for the management of devices such as phones, tablets, laptops, and desktops supporting many different use cases coupled with well-defined processes, molded to your organization’s security and application needs, to enable productivity while reducing potential security risks.
We look at well-defined processes that are molded to your organization’s security and application needs to ultimately drive productivity and reduce security risks.
The Maturity Model
We rate Unified Endpoint Management maturity through our proprietary Maturity Model. This maturity model has some common phases in it that aren’t something that we’ve developed and should be somewhat recognizable.
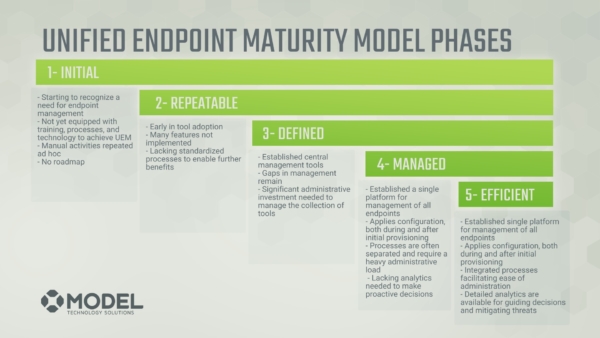
The five phases of the maturity model are:
Initial
You’re starting to realize you have a need for growth and maturity.
Repeatable
Where you’re early in that adoption, you have many features that are not implemented yet, and you’re lacking standardization around processes to enable further benefits.
Defined
You have established central tools but you still have some gaps in management and it requires a lot of administrative investment.
Managed
You have that single platform of a single tool for your endpoints. You apply configuration, both pre-provisioning and post-provisioning. However, your processes tend to still be pretty require a lot of heavy administrative effort. And you’re lacking the aggregate of the analytical data to make some strategic decisions in the organization.
Efficient
You’ve got that established single platform and you’re applying configuration pre and post-provisioning. You’ve got integrated processes for administration, making it super easy. And you have a lot of analytics that are driving the strategic decisions in your organization.
The Model Technology Maturity Model then narrows in on those phases and how they overlap onto five categories for device management. We’ve defined five device management categories including:
- Management Infrastructure
- Configuration Management
- Updates and Servicing
- Application Management
- Endpoint Security
Each one of those topics themselves have many different sub-categories.
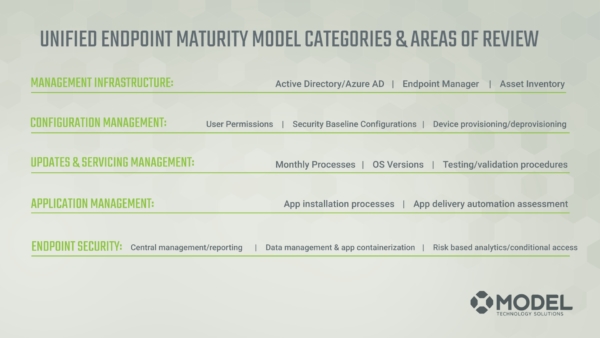
Each of these categories will be covered in-depth through one of these sessions in this series.
What Does It Look Like?
What does Management Level 2 look like practically in an organization’s infrastructure?
- Devices may be joined to active directory or Azure active directory.
- Users are being managed in that central directory.
- You have some initial configuration capabilities, but you’re not necessarily actively managing it or it’s not kept up to date.
A good example of that would be that maybe you have some configurations in group policy or some containers or OUs created in active directory but then you never manage them further. People go in there, devices go in there, and that’s just where they live.
- Loose processes might exist for configurations.
- The infrastructure has a lot more capabilities than what it’s being used for.
- Many configurations or deployments are still manual.
- Often times at this level your employee’s internal tool set expertise can be lacking because they’re generalist. One person is doing many jobs, resulting in heavy administrative effort. That’s because those individuals are burdened with many tasks and responsibilities.
Bottom line, the foundation exists that could facilitate so many other areas of strategic growth and tool implementation, but you’re still at that very basic level. As devices get provisioned, they go into active directory and they get moved to the OU. That’s why it’s a repeatable phase: you know what to expect out of a device, but there’s still a lot of room for improvement.
