Welcome to another installment of Model’s approach to Unified Endpoint Management. This is part of a series of posts and videos we’ve done about our proprietary approach to UEM and the different stages of maturity in the categories of our maturity model. You can find the Maturity Model videos playlist on YouTube here.
In today’s post we’re going to cover:
- Our running definition of Unified Endpoint Management
- A brief review of our proprietary Maturity Model
- An brief explanation of what it mean to be a Level 5 maturity in your Configuration Management
What is Unified Endpoint Management?
The standard definition of Unified Endpoint Management is…
…a single platform for management of devices such as phones, tablets, and desktops supporting many different use cases.
At Model Technology Solutions, our definition expands on this a little bit:
Model’s Definition: A collection of processes supported by technology for the management of devices such as phones, tablets, laptops, and desktops supporting many different use cases coupled with well-defined processes, molded to your organization’s security and application needs, to enable productivity while reducing potential security risks.
Our definition, in addition to the platform, also includes processes that take into account your organization’s security needs, application needs, and personas. The ultimate goal of Unified Endpoint Management is to enable productivity while reducing any potential security risks and minimizing costs, and the processes that you implement are as much a part of that as the platform that you use.
Our Maturity Model
Model’s maturity model uses five stages or phases to define endpoint management characteristics.
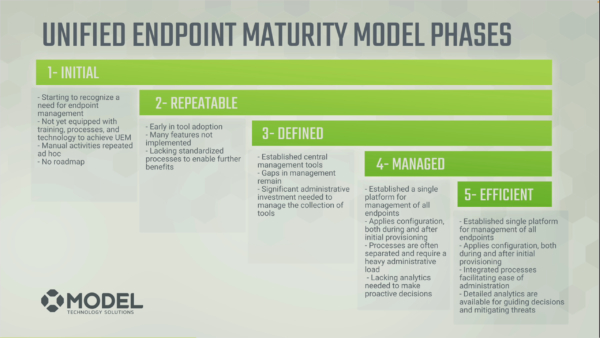
- Initial phase: You’re starting to recognize that you have a need for a unified solution to manage these tasks.
- Repeatable phase: You’re doing things the same way, repeatedly, over and over again, which improves efficiency and security.
- Defined phase: You have intentionally created robust definitions on how things are being done.
- Managed phase: You are in a state where your endpoints are fully controlled.
- Efficient stage: Your processes are highly-defined, and you’re gathering and using deep analytics to drive those capabilities and improve on your management.
These phases rank our five categories for endpoint management.
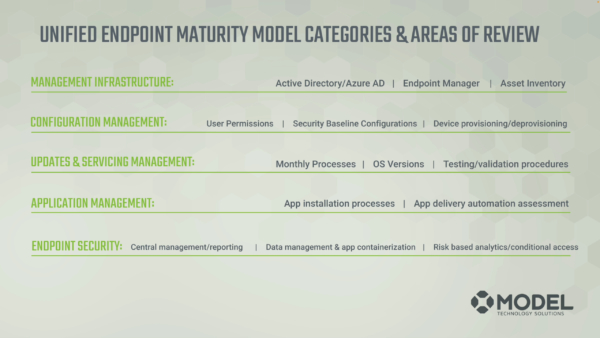
These categories include:
- Management infrastructure
- Configuration management
- Updates and servicing
- Application management
- Endpoint security
If you’d like more information on any of these categories or their different phases, be sure to check out the playlist linked at the beginning of this post or find previous posts from the series on our blog.
In today’s post we’re going to dive into Configuration Management and what it looks like to be at a Level 5 maturity in this category.
Configuration Management Level 5
Configuration management (CM) tools are a necessity in any size organization. CM tools help prevent unwanted changes in the environment, enable you to control the user experience, patching processes, software deployments, and many other functions. In enterprises, the administrator typically uses the CM tool to setup a baseline configuration or set of settings for the users. This creates a predictable space for their work to be completed while staying within the boundaries of security and compliance requirements. While this landscape has changed in the modern world, the need for a configuration system is still very much a necessity.
At a level 5:
- Provisioning processes are robust, well defined, and potentially even automated (or are at least more automated than they are manual).
- Endpoint configuration is thoroughly defined by role.
- Configuration drift is managed, meaning that when a machine is put out on the floor, it is maintaining the security and configuration posture you put together.
- Robust self-service capabilities exist.
- Deprovisioning processes are well defined and potentially automated.
Provisioning Processes
Whether you have machines on-prem, in the cloud, or are repurposing a machine, provisioning can look very different.
Organizations that aren’t very mature in this category may be building machines by hand or buying them from different vendors and then just handing them out to users. The time you acquired the machine might dictate what apps or configuration you have installed. This is the lowest, most basic level of the provisioning process, if one could even call it a “process”.
In a highly mature environment, however, your Configuration Management becomes far more refined.
If you’re using the cloud to do your provisioning, you might be autopiloting and presenting a lot of optional applications to the end user for consumption. Even if many of your applications are SAAS-based or you have some that need to be installed, they are installed within an hour of the user logging in, if not prior to the end of autopilot being provisioned.
In an on-prem environment, you might have a interface like Model’s Dynamic Deployment Interface (a tool created to replace the User Driven Installation wizard) which provides a robust set of applications and standard configuration sets for devices.
For example, say you’re a user in a marketing department. You want a machine that has all of your marketing tools installed and the machine to have whatever permissions it needs to do your job. In a re-provisioning process, you would either reset the machine and let it autopilot, or in an on-prem environment you’d re-image the machine based on the configuration profile you chose.
Endpoint Configuration
However, to get to that point, you potentially have to define your configurations by role. Defining this role-based configuration is a sure sign of a high-level of management maturity in Configuration Management. In the graphic below, you have a variety of different people, resources, or personas in your environment. Those people potentially need different applications and machine types to do their job effectively. If this process is not well defined (unless you are familiar with the environment that machines need to be applied to) users can get very frustrated when you provide them with a new machine.

In Configuration Management Level 5, app deployment is standardized. People in the project management department get Microsoft project and maybe Power BI. Whereas in financial management, they might get access to the ERP system and Power BI instead.
In role-based configuration, the simpler you can make the roles the better. Both small and large organizations can have lots of complexities in defining roles, but ultimately what you need to do is learn what end users need and provide a configuration process that enables productivity. Your users need to have the right apps at the right time, every time, so that they can get to work and not spend time twiddling their thumbs waiting for their apps so they can get to work.
Managing Drift
Once the initial provisioning process is completed, or a setting has been deployed through some mechanism in your environment, that setting is now always applied at a snapshot in time, for example during the provisioning process, an update, a refresh, or a login. This includes things like:
- Configuration Profiles
- Baselines
- GPOs
- Automations
There are many ways to provide these settings. However, making sure they are applied, reapplying them if necessary, and validating that they need to be reapplied is the only way to ensure a consistent operating environment.
Oftentimes IT teams want to provide the initial configuration and let users change it from that point forward. That is certainly an acceptable way to do it, to a point. After that point, you always want to be able to control certain elements of the operating environment all the time. While you might give users options for customizable elements, you still want an overall control of these elements that is managed from your IT department.
Self-service Capabilities
Another element of Level 5 Configuration Management is a robust set of self-service capabilities to your end users. This includes:
- Applications for installation, whether you’re in a cloud or on-prem environment
- Updating the operating system to the next version from both a security patch and an operating system perspective
- Requests for non-sanctioned apps
- Password resets
The ultimate idea here is to give users authority and customizability to the best of your ability. You want to try to minimize the amount of requests that they need to make to you, so that they’re able to be as self-sufficient as they can during working hours. In the end they’re happier, your infrastructure is more efficient and secure, and you have more time to allocate that you’re not spending manually provisioning and configuring devices.
Deprovisioning Devices
Often the deprovisioning process we hear about people using is, “Hey, go ahead and hand your machine to Jim over there, and he’ll take care of it.”
Now, Jim might run a DOD wipe, or he might not. He might let the machine sit, or he might just reimage it for the next user. Without a good life cycle management process from provisioning to deprovisioning, you can create non-ideal situations in your environment like:
- Data leaks
- Breaches
- Inaccurate inventory
If you just reimage or autopilot a machine and hand it to somebody else when a user moves on from the organization, that’s poor life cycle management. The age, usability of the device, and when the device is getting retired should all be taken into consideration during the deprovisioning process. Many of us take this for granted and just retire or reprovision the machine. There’s a lot of things that can go into a discovery to ensure that you’re doing a service and not a disservice to the organization. A solid deprovisioning process takes into account the age of the device, the use case of the device, and the data wiping processes for a retired device to name a few. While this process is similar from organization to organization, the details will vary.
Benchmark Your IT Maturity
All of these elements are the essential elements to highly mature Configuration Management in your environment. But how do you get there? You need to start with a benchmark of where you’re at then develop a roadmap for where you want to be, and we’d love to help with that. Our IT Maturity Health Check service is a perfect way to assess the maturity of your infrastructure across the board. With this data, you can then identify the best categories to improve and projects to implement in order to improve your maturity, and reap the benefits that result from it in security, compliance, and cost-effectiveness.
Practically what this service looks like is:
- A short questionnaire
- A 90-minute onboarding
- A 90-minute review session
Our first 90-minute session will help us get a deeper understanding of your environment. We’ll review everything from business operations, alignment, challenges, roadblocks, user adoption of new technology, and talk about specifics of where you’re at from a technical and a tactical standpoint in each of the categories.
Using your questionnaire and the information from this session, we’ll create a findings and a prioritized recommendations list that we’ll deliver in the next 90-minute session. You will also have the opportunity to ask any questions about how we operate or about the report. The information delivered during the second session will help you identify projects you could use to improve your maturity.
If you’d like to learn more about the Health Check, you can follow the links in this paragraph. Many of our current clients have gone through the Health Check and found it to be a tremendous value.
Questions? Feel free to reach out! You can use our contact page, or you can email me at Jason.ruthford@model-technology.com. Always happy to chat!
