Howdy! I’m going to make this blog short and to the point because this topic can be cumbersome and intimidating to approach. It was difficult finding a concise blog giving me all the answers I needed. The scenario is a customer was wanting to manage SCCM agents across non-trusted domains, potentially across firewalls, while using System Discovery, leveraging client push, and all without certificates.
I’m going to hammer on the main points… Managing non-trusted domain machines does not require certificates and managing these machines can be achieved in a couple of easy steps:
- Ensure you have name resolution to the non-trusted domain machines
- This can work differently per environments, but in conditional forwarders and/or DNS suffix search orders work pretty well in establishing name resolution between different environments.
- You could also use hosts files, but…
- Ensure you have the necessary ports opened. Ports vary based on what site server components the machines will need to access.
- Current Branch Ports
- Don’t forget telnet is your friend here
- Have an domain install account for each domain you wish to manage (client installation account)
- The account will need administrative rights on the machines (for client push)
- Extend the AD Schema in the remote domains with EXTADSCH.exe
- Have an domain account with permissions to publish to the System Management container in each domain
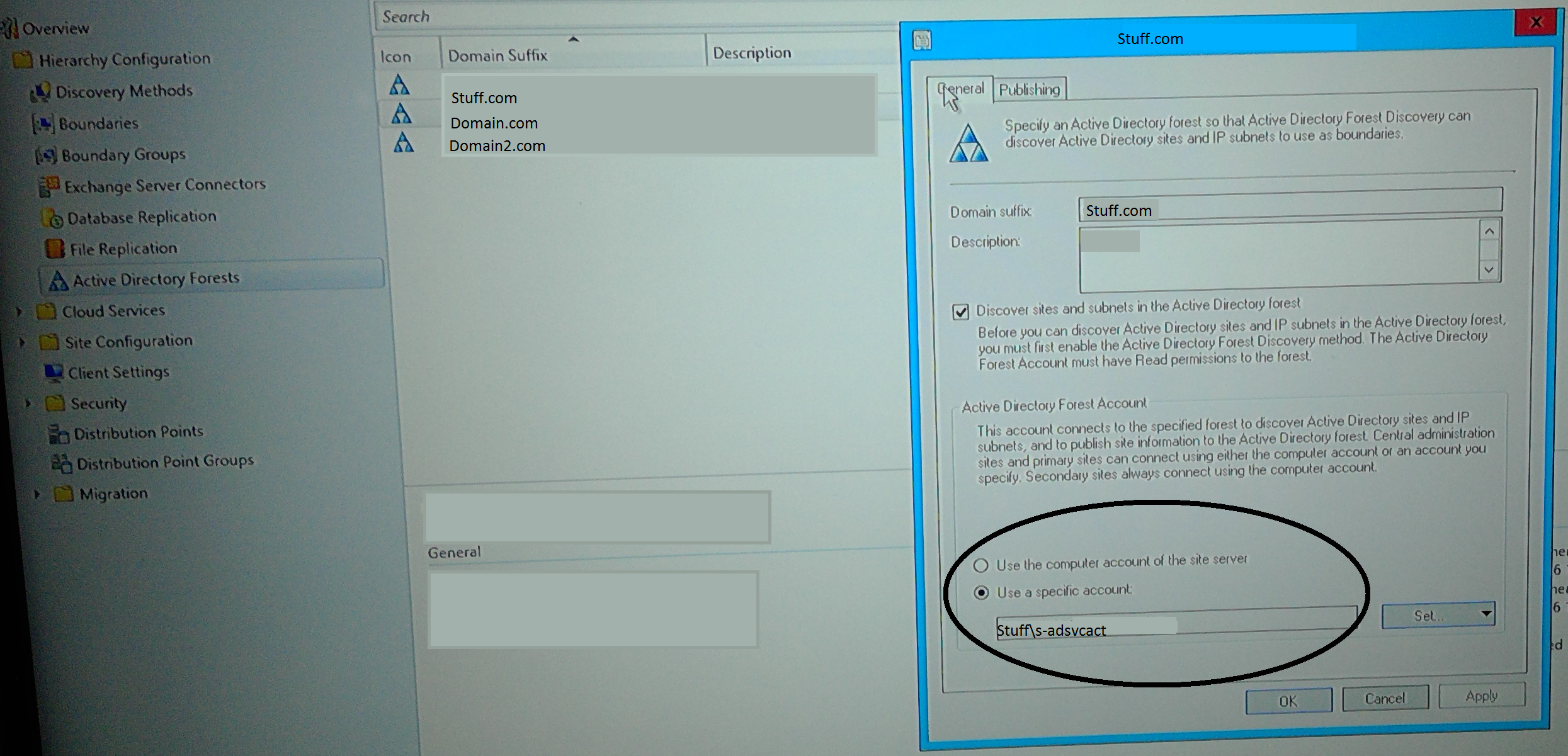
- Setup the forest publishing
- In Hierarchy config, add the forest and accounts as seen in this super awesome screenshot which has not been modified in any way:

- Ensure on the publishing tab (not shown above) you have it set to publish and the domain specified.
- Create discovery rules for each of the domains
- For non-trusted domains, you’ll need to use an account that’s in that domain to run the query against AD
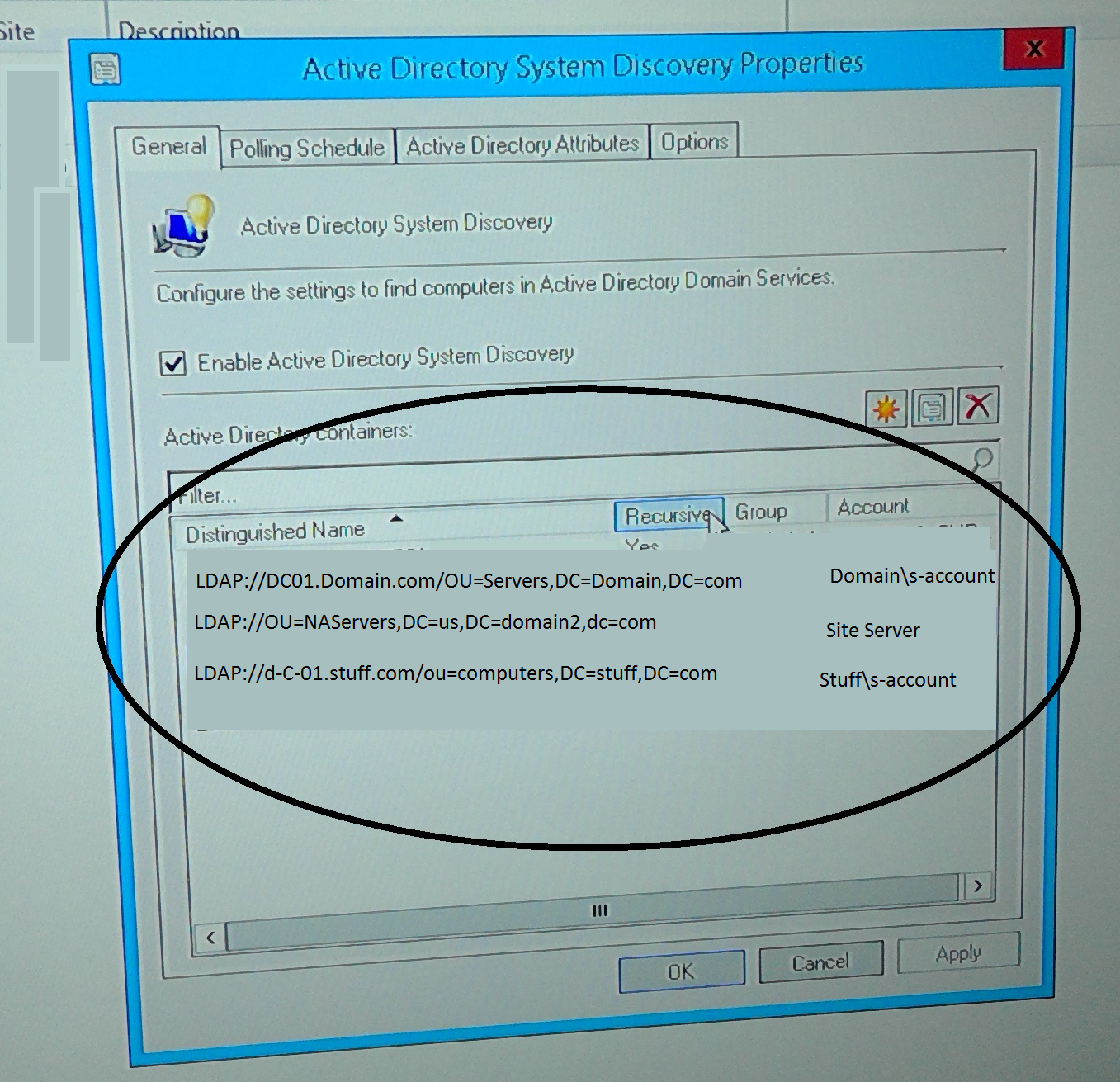
- Under ad System discovery
- Click the Star for a new discovery rule
- NOTE: you won’t be able to browse for the un-trusted domains, so you’ll need to type the LDAP language starting with server name
- LDAP://DOMAINCONTROLLER.Stuff.com/OU=SomeOU,DC=stuff,DC=COM
- As seen here in a depiction of what a discovery rule would look like done by someone who studied abstract art in college.
- Click the Star for a new discovery rule
- In Hierarchy config, add the forest and accounts as seen in this super awesome screenshot which has not been modified in any way:
Once the discovery has ran, you’ll be able to install the clients using the client push. One piece to note is that the infrastructure will move through the list of the client install accounts which may create a number of failures in the ADSYSDIS.log. Also if you’re using boundaries, don’t forget to add the boundaries!