Welcome to Model’s approach to Unified Endpoint Management Maturity Model overview series! My name is Jason Ruthford and I’m the managing partner of Model Technology Solutions. Today, we’re going to be reviewing Endpoint Security Level 3 (Defined).
In this post, we’ll:
- Talk about what Unified Endpoint Management means
- Review our own proprietary maturity model
- Talk specifically about Endpoint Security Level 3
What Is Unified Endpoint Management?
Let’s talk a little bit about what Unified Endpoint Management means in general. A standard definition of Unified Endpoint Management is a platform for management of devices such as computers, phones, tablets, servers, etc.
Standard Definition: A single platform for management of devices such as phones, tablets, laptops, and desktops supporting many different use cases.
At Model, we look at it just a little bit differently. We take that same approach but we simply add to the definition the well-defined processes that adapt to your organization’s security and application needs to enable productivity and reduce potential security risks.
Model’s Definition: A collection of processes supported by technology for the management of devices such as phones, tablets, laptops, and desktops supporting many different use cases coupled with well-defined processes, molded to your organization’s security and application needs, to enable productivity while reducing potential security risks.
The UEM Maturity Model
At Model, we’ve created a proprietary maturity model related to UEM. We incorporated five phases which are commonplace in our industry, have been around for quite some time, and we adapted them to UEM strategy.
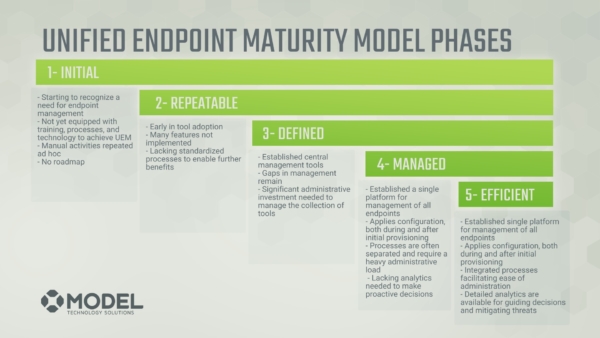
Those categories and their brief definitions are:
Initial
You’re starting to recognize a need for enterprise endpoint management.
Repeatable
You’re in early in tool adoption, but many features are not yet implemented. You need some standardization around processes to really further enable the benefits of the tool set.
Defined
You’ve got an established central management tool that you use. There are some gaps in the management, some features that are not necessarily implemented yet, and it still may take a potentially significant amount of administrative investment needed to collect data and manage the tools.
(This defined level is what we’re going to spend some time today focusing on in Endpoint Security.)
Managed
You’ve got the single platform for all your endpoints. Maybe you are applying configuration pre- and post-provisioning. However, processes are still requiring a lot of administrative effort and work hours to execute. Maybe you’re still lacking some analytic data to help drive those strategic decisions in the business.
Efficient
You’ve got the Unified Endpoint Management platform, you apply your configuration and processes that are well-defined makes administration life easy. You’ve got detailed analytic data to help guide your decision making processes.
Once we defined these phases, to complete our model we applied five categories on top of them that we see as pertinent to endpoint management strategies:
- Management infrastructure
- Configuration management
- Updates an servicing
- Application management
- Endpoint security
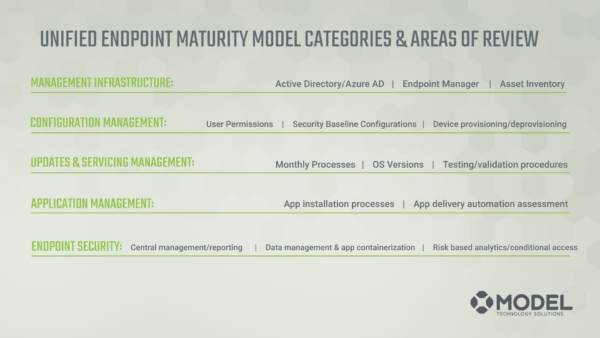
We’re going to spend time today on Endpoint Security level three from a high level.
Endpoint Security Level 3 (Defined)
Let’s talk a little bit about a high level overview of Endpoint Security.
Again, the repeatable state of endpoint management is where you are “in early in tool adoption, but many features are not yet implemented. You need some standardization around processes to really further enable the benefits of the tool set. ”
Inefficiency, over-complexity, and poor security may still be a problem with Level Two Endpoint Security. In order to improve in these areas, some solutions regarding endpoint management maturity are:
- Threat and vulnerability management
- Reducing attack surfaces
- Next generation protection
- Endpoint detection and response
- Automated investigation remediation
These are things that you’ve probably heard of that are kind of buzzing around in our space and have been for quite some time time. But this is really just the tip of the iceberg when it comes to Endpoint Security. There’s a whole security architecture specifically from Microsoft around endpoints and cloud data these days that can help you improve in this area.
However, for the purposes of this particular video, we’re just going to cover a high-level of a few possible solutions.
Threat and venerability management is the ability to discover vulnerabilities and prioritize those risks based on your environment. This is an important step.
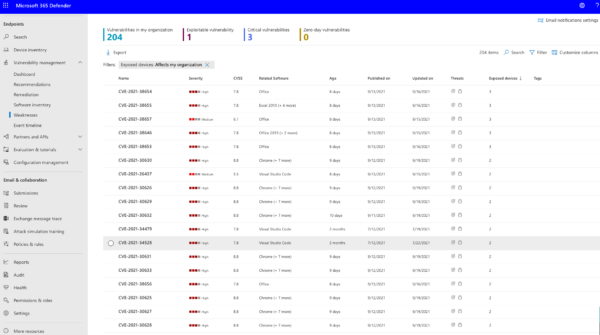
Here’s a screenshot of a more mature environment when it’s looking at Windows Defender for endpoints. This level enables ability to see what devices and software have vulnerability. Having these tabs together allows for your team to make decisions quickly.
It’s really just adding some intelligence around that threat and vulnerability management. That versus wait for a scan to happen, waiting for the inventory to come back from that scan, and then taking action on only who is missing that patch once they’ve realized they’ve missed that patch. It’s a very different approach.
Next, hardening the potential risks that are based on an organization includes, for example:
- Hardware based isolation thorough containerization
- Preventing unapproved applications through application control
- Using controlled folder access provide additional layers of security that allow only specific apps to allow specific data
Each of these tasks take a whole lot of tool sets and processes to implement, however, which is why these processes require a Level Three to actualize.
Ultimately the end goal is to reduce the overall attack surface or potential impact to the organization by leveraging your tools you installed at Level 2 Endpoint Security.
Finally, next generation protection. Some actionable strategies in this area are:
- Behavior based antivirus
- Cloud delivered protection
- Block at first-sight protection
- Potentially unwanted applications protection
What this all really boils down to who is not just using definite file-based definition threats. We’re able to account for things like memory-based threats, events, applications, processes and network connections. Blocking things out of the gate that you haven’t even defined yet (e.g. malware) that are browser-based.
You ultimately do this using something like the Potentially Unwanted Application Protection that you get through Chromium or Microsoft Edge.
These are all just examples. Ultimately, your ability to step up the Endpoint Security game by starting to more-effectively use your tools gets you to Level Three Endpoint Security.
Steps To Level 3 Endpoint Security
There’s a whole lot of different terminologies that were referenced in this post. Of the five steps that we mentioned here we only covered three of them in a very high level overview today. The point of this post is not to explain them all or to give you a deep dive into the concepts.
If you’re really interested in improving your Endpoint Security in a deeper way, I would suggest doing the following:
- Ensure that you have a well defined security strategy for your endpoints and cloud data
- Check that you have tools that are capable of executing those kinds of features
- Identify where you’re at currently and what gaps you have in your security
- Prioritize gaps with a list of remediation actions that you could execute
What this will do for your is determine your move-forward strategy for Endpoint Security.
The Maturity Model Assessment
This video serves as a maturity model overview for a more detailed offering that we offer. As part of our Maturity Model Assessment, our engineers will assess your Management Infrastructure, Configuration Management, Updates and Servicing, Application Management, and Endpoint Security through the lens of our maturity model.
From this assessment, we’ll create a findings and recommendations report that can help drive your organization forward in the endpoint management game. Essentially, if you want an assessment of where you are done but don’t have the time to do it for yourself, we’ll be happy to do the legwork for you.
Practically the assessment consists of two 90 minute sessions and some discovery paperwork. Once we complete your assessment, you get a findings and recommendations report that’s a prioritized strategy for your organization.
The assessment will help you get your organization to the Endpoint Security (and other categories) level which you need to be.
We’d love the opportunity to make your life easier (and more secure!) through one of these assessments. You can learn more about the offering by clicking here.
Until next time, thanks from the entire team here at Model Technology Solutions! Keep fighting the good fight. We’re in your corner.
