This post is a short overview of how you can use Microsoft Defender for Identity to investigate high-alert users in your environment.
If your active directory is a little bit spread out, using Microsoft Defender for Identity will allow you to track user access to files and folders. Defender has powerful capabilities to let you know which users are high-alert, investigate them and, if necessary, change their privileges to maintain security in your environment. This will ensure that sensitive data is protected by verifying that users only have the access that they need and nothing more.
This ability to investigate high-alert users is what we’re going to cover in today’s post. Let’s dig in.
Using Defender for Identity to Track and Investigate User Access
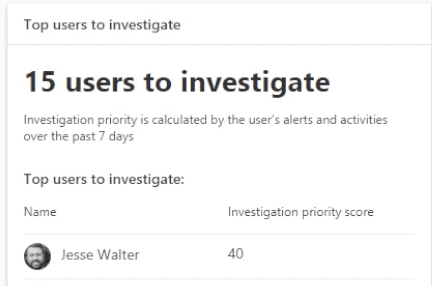
There are several ways to access Defender for Identity and investigate users. The most common way is to go through the portal.cloudappsecurity.com. In the example below, you can see that there are 15 users to investigate. This information is based on any investigation priority that Microsoft has analyzed and collected over the past week.
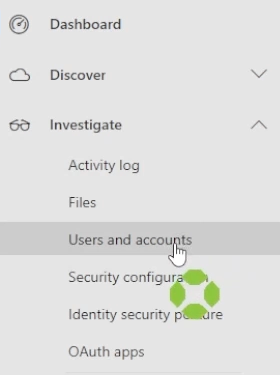
If you expand the menu on the left, you can then go to investigate and select users in accounts.
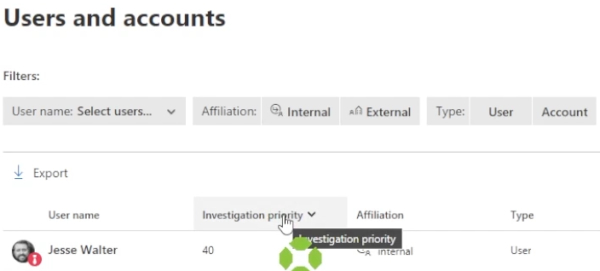
Now click on investigation priority to sort. The higher the number, the more at risk a potential user.
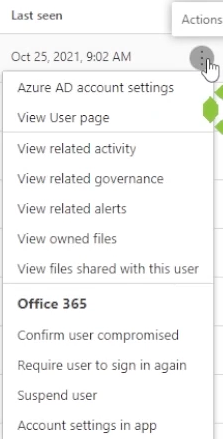
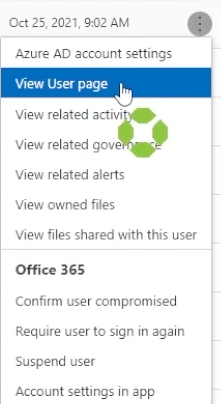
The action menu over to the right allows us to do a number of things, including view the user page and any related activity or alerts that may have been generated by any user action.
Here is an example of an alert generated by a user account.

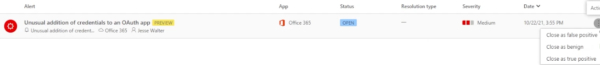
Alerts can be marked as a false positive, benign, or true positive.
Before selecting an action, it’s best to dig into the alert a little more.
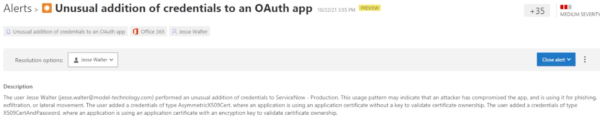
By clicking on the alert, you can see that it was generated as the user was attempting to connect Azure active directory to ServiceNow for single sign-on.
Going back to users and accounts and view the user page.
Here, you can see exactly why the investigation priority score is much higher than the rest of the organization, as the weight given to the unusual addition of credentials to an O off app is 35, which is very high.
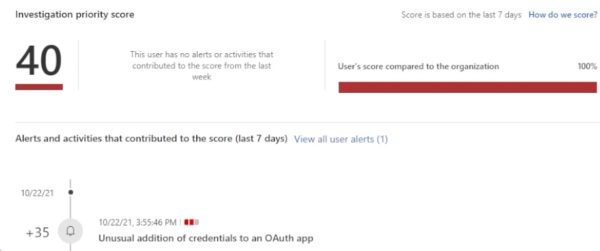
In this example, since there is an unusual addition of credentials to the O off app, you could confirm the user compromised…

…or go to the account settings in Azure active directory and revoke all current sessions, forcing this user to have to log in again.
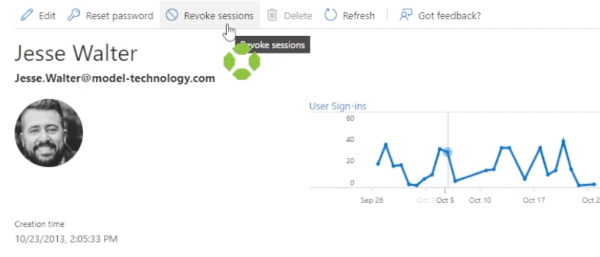
But because this was not a malicious activity, this particular alert can be closed as benign under alert actions.
And that’s it! For further information about how to use Microsoft Defender for Identity, you can visit the Microsoft Documentation about this software. Or for more information on how you can track your identity profiles and limit access to sensitive information, we can help as well. Feel free to reach out to us at www.model-technology.com/contact-us.
