In this post, we’re going to talk about how to protect your organization from unsanctioned applications using policies with Microsoft Defender for Cloud Apps. You’ll read a high-level overview of Microsoft’s CASB solution, Microsoft Defender for Cloud Apps, and specifically how you can leverage it to mitigate your company’s risk from Shadow IT.
What Is Shadow IT?
Shadow IT is defined by Gartner Glossary as:
IT devices, software and services outside the ownership or control of IT organizations.
Shadow IT is when users in your organization install unapproved apps, potentially opening the workplace to vulnerabilities that are difficult to mitigate. How this looks to the IT team is you might be that you have a difficult time getting a solid grasp on what applications are installed in your environment, especially if many of your users are local admins.
A real life example of Shadow IT would be your users setting up their own cloud apps because they do not care for, understand, or know the solutions you have approved for your environment. Maybe you’re trying to implement OneDrive for business for your organization as a file repository. Your users don’t understand how to use OneDrive for business, but they’re very familiar with Dropbox. So instead of leveraging OneDrive for business, they install Dropbox and start using that tool.
The risk for potential loss of data or exposing your private IP publicly goes up exponentially when users leverage tools that are not approved within the environment. However, Microsoft Defender for Cloud Apps gives us the capability to identify applications that are installed (otherwise you might not have been able to see how often they’re being used) and create next steps so that you can either trust these apps or blacklist them completely.
A Look Into Microsoft’s CASB Shadow IT Prevention
Microsoft Defender for Cloud Apps, Microsoft’s CASB solution, provides ways to mitigate Shadow IT in your organization. If you go into discover and the cloud discovery dashboard, you can see that we have discovered 219 apps within your environment. Microsoft takes the discovered apps within your environment and cross references it with 16,000 apps in their catalog that they continuously add to, to determine what is commonly viewed as a potential risk or identified as a low risk profile.
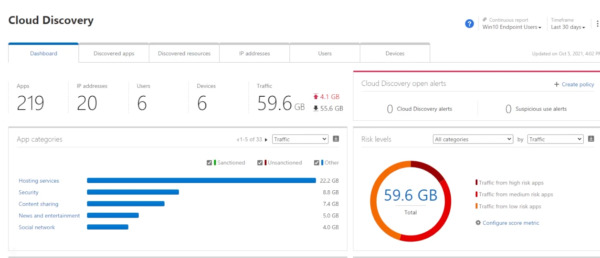
So you have a list of 219 discovered apps as we saw in the dashboard which you can access by clicking the apps as well.
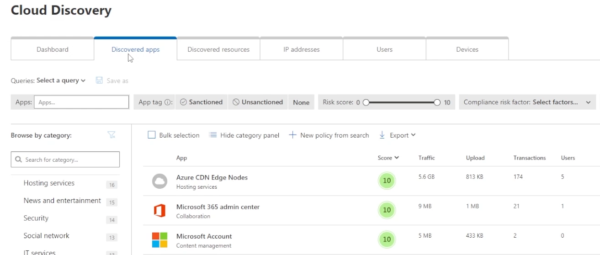
You also have a number of filters at the top. The “Sanctioned” and “Unsanctioned” buttons allow you to identify applications that are approved or not approved in your environment and what kind of alerts they generate.
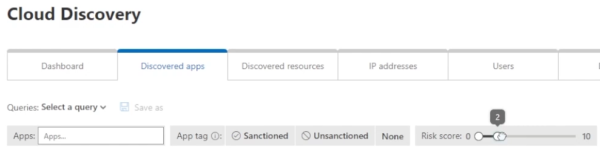
You can also filter by the previously determined risk score. If you decrease the risk score, you’ll see some higher risk applications in our environment. This allows you to get really deep into apps that are potential threats in your environment and sanction or block them.
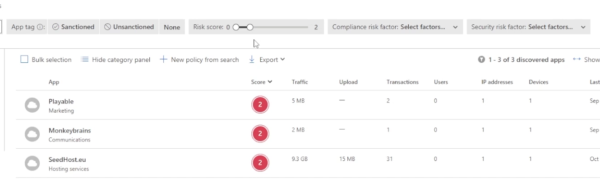
One of the most helpful features here is the alerts. If a company identifies that there has been a breach, Microsoft gathers that data and then alerts you. Essentially there is always somebody keeping eyes and ears open to determine whether or not there has been an exposed threat for any application run in your environment.
You can also see why particular apps are dangerous. If you wanted to know why a particular app received a score of two, you simply click on it in CASB and you can see the different categories Microsoft uses to determine the risk factor. This gives you an idea of how to assess where exactly the risks could be in a specific application and how to best sanction or unsanction the app.
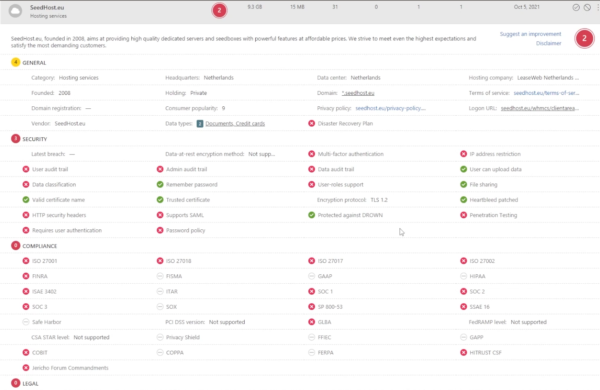
At the far right, you can also use the circular icons to:
- Mark the app as monitored
- Override the app score entirely
- Add notes for other admins to read or edit the app details
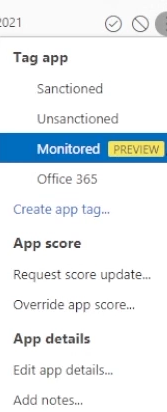
Additionally, you can edit the app details and use this with conditional access app control to get a more real-time perspective into the usage of this app. Edit the details, hit save, and mark the app as monitored.
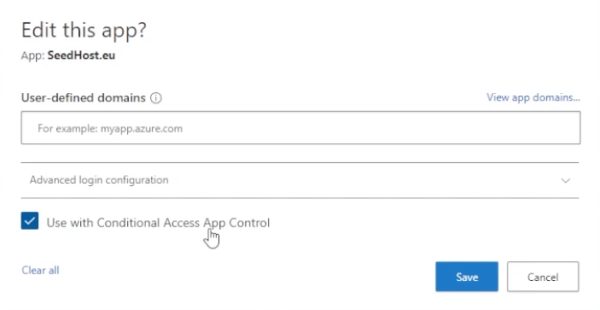
Afterwards, you get this prompt. A warning message is displayed to users upon accessing monitored apps.
You can click on the link and go into cloud app usage here. If you click on devices…
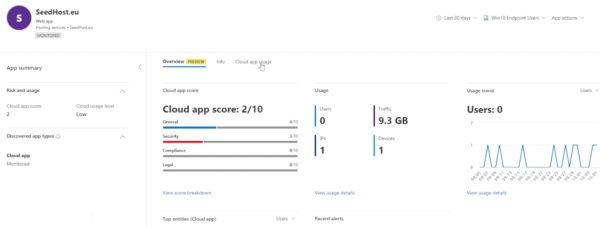
…you can now see which device is being used to access that application.
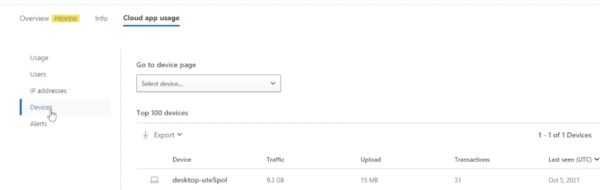
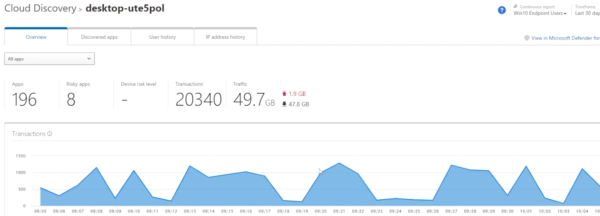
From there, you can drill into more specific information as to the traffic user history, IP address history, and get a general idea of what this application is doing in our environment, as well as view the information in Microsoft Defender for Endpoint.
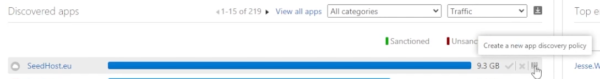
Going back to the dashboard, go down to the discovered apps widget. You’ll notice that if you hover over it, you have the capability of tagging a specific application as sanctioned or unsanctioned, or you can create a new app discovery policy.
Now you can either choose a policy template or create a new policy from scratch. For example, you could create a policy that monitors any app you put into the monitored state or tag with monitored. Mark the severity as medium, put in a description, and add filters.
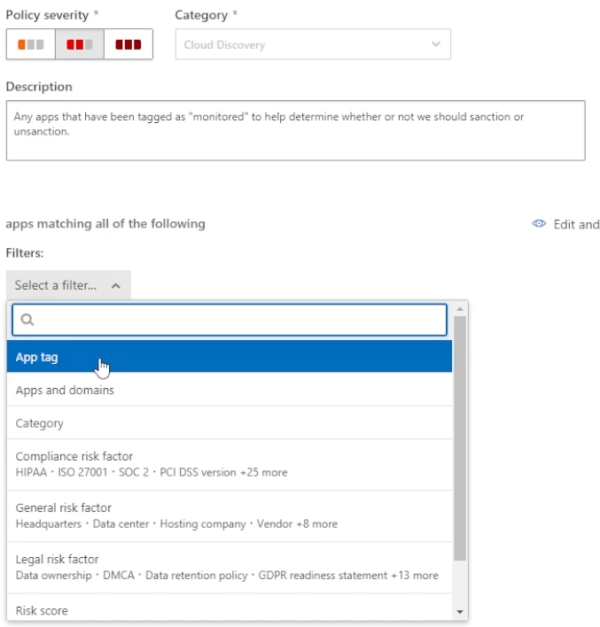
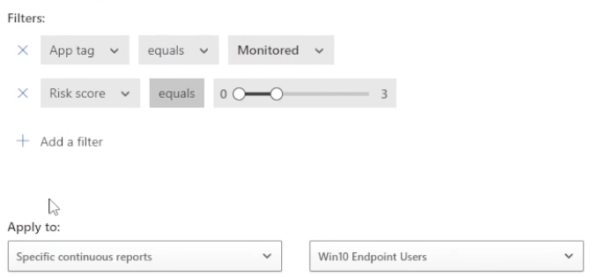
For example, the app tag filter. If the apps are monitored with the risk scores between zero and three, you can apply this to all continuous reports or a continuous report that we define. Since we recognize that this app was our highest traffic generator, you want to trigger a policy match for monitored apps with a risks score from zero to three and daily traffic is greater than 5,000 megabytes.

We can then create an alert for each matching event within the policy severity.
Another feature is you can send alerts to power automate, which allows you to create a playbook that will automate a response. For example, creating a blast to a specific team in Microsoft teams.
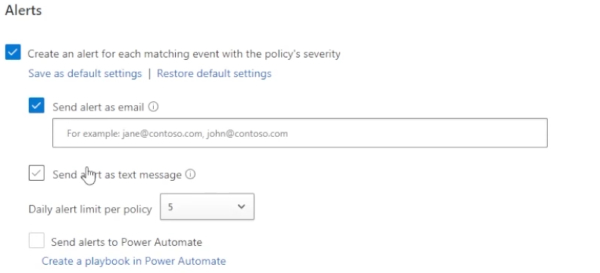
Finally, you can apply a governance action that tags the application with a sanction or unsanctioned or monitored, etc. Since this is a policy that is specific to a monitor app, we will leave that alone and then we’ll create.
Now we see our policy has been created and we can continue to edit the policy as we see fit or view all of the alerts that are generated by this policy.
This is a mid-level introduction to managing Shadow IT with Microsoft Defender for Cloud Apps. If you want to learn more about this process, you can read the eBook from Microsoft that talks more about everything we’ve talked about today.
EBOOK: Discover And Manage Shadow IT
You can also read more about Microsoft’s CASB in general in this Microsoft documentation.
