These days there’s many paths that outside attackers can attempt to break into your environment. But by far one of the most-effective methods is by simulating trusted entities, such as a credentials harvest attack. According to Uniken, credential harvesting is:
…the use of MITM attacks, DNS poisoning, phishing, and other vectors to amass large numbers of credentials (username / password combinations) for reuse.
This could look like an attacker simulating a familiar login screen in order to trick users into voluntarily entering their user name and password which would then be sold or used for malicious purposes.
Microsoft Defender has tools for testing and remediation of problems that could lead to an attack like this. And in this post, you’re going to learn how to use Defender for Office 365 to simulate an attack and then improve the security in your environment based on Defender’s recommended actions.
Let’s dig in.
How To Simulate A Credential Harvest Attack in Microsoft Defender
If your organization has Microsoft Defender for O365 Plan Two, you can use Attack Simulator in the security and compliance center to run a realistic attack scenario in your organization. An attack simulation can help you identify and find users in your environment that might be vulnerable to a real attack before one actually impacts you.
To simulate an attack, first go to security.microsoft.com and enter your portal. From there, under email and collaboration, choose attack simulation training.
After being redirected, launch a simulation.
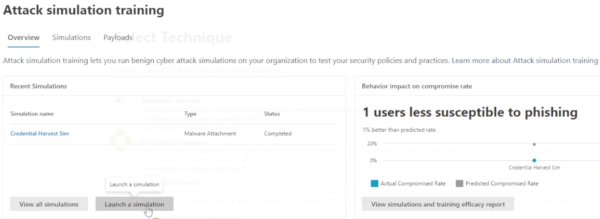
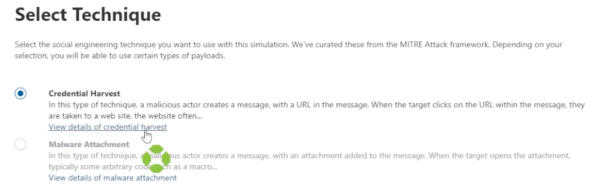
The next step is to do a credential harvest. If you want to see details of what a credential harvest is, click on the link and a description goes through the simulation steps.
First give it a name and a description.
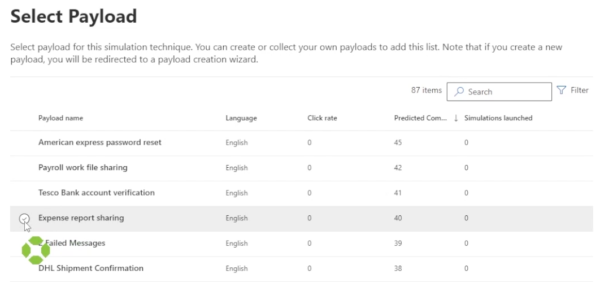
A list of payloads that you can select from will come up. Sort by predicted compromise rate, and select one that may be a good candidate in your environment.
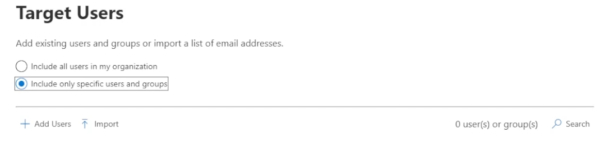
Choose whether to send this to all users in the organization or include only specific users in groups.
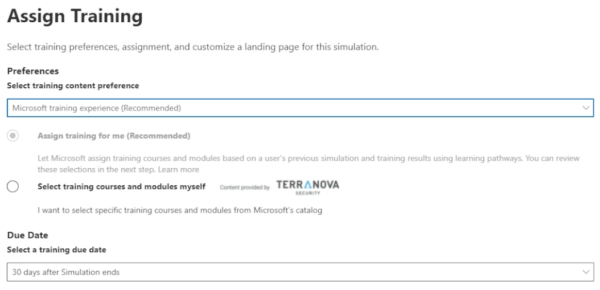
Once users have been selected, you will choose whether or not to assign any training if a user did prove to be vulnerable.
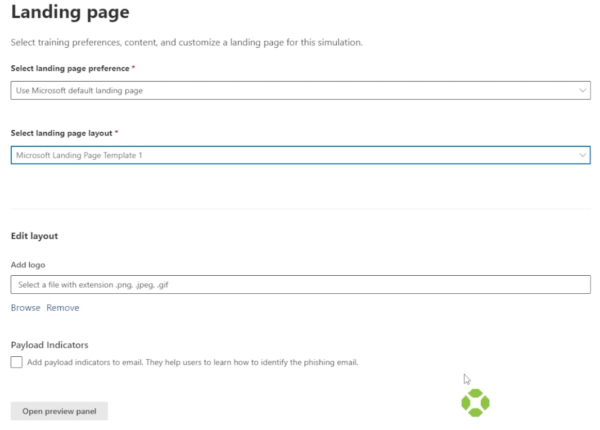
You can customize the landing page for when a user selects the email, add a custom logo, and view both with the preview. You will also be able to set how long the simulation will last.
After submitting, you will receive an email. If the user selects open, you will be brought to a sign in page.
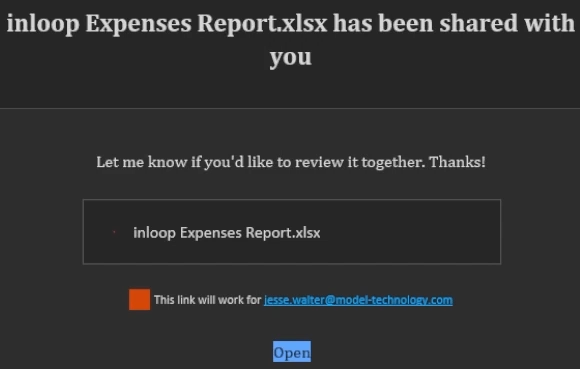
Enter in the user and you will be brought to the landing page you configured.
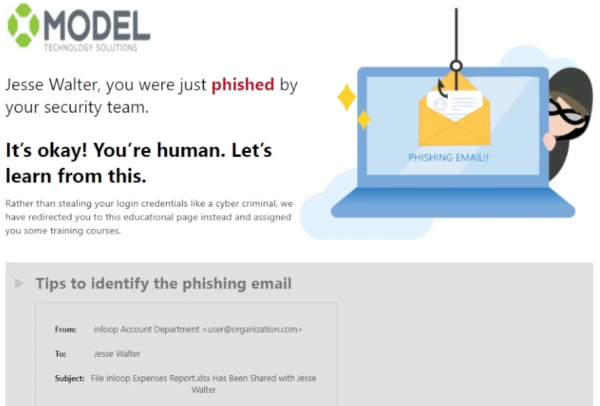
This data is sent back to Microsoft Defender for O365, where you can view which users who were part of the campaign are the most vulnerable. Go back to the attack simulation training page and click on the most recent simulation.
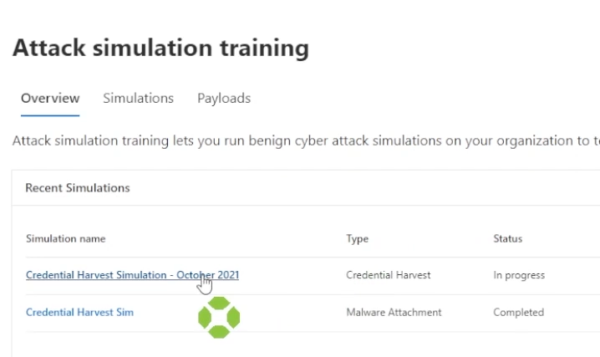
Here you can already see that an email link was clicked.
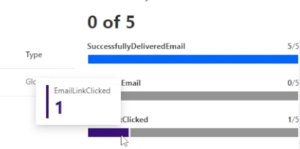
The testing is complete. But based on the results of this test, improvement actions recommended by Microsoft can be taken to increase your secure score and improve the security of your environment.
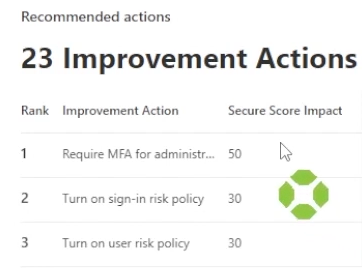
From here it’s your responsibility to implement and assign tasks and trainings to make sure that someone less forgiving than your team doesn’t phish your end users with the real deal!
For more on this simulation and other simulations possible in Microsoft Defender, you can read the Microsoft Documentation here.
For more information on how you can further protect your organization from potential email vulnerabilities using defender for O365, please contact us.
