Navigating the digital landscape demands more than passive measures; it calls for a proactive security stance. For IT directors at mid-sized organizations, staying one step ahead of cyber threats is not just a strategy, it’s a necessity. With remote work on the rise, and more tools than ever – regular, proactive maintenance of your network isn’t just recommended, it’s required.
Understanding the Threat Landscape
With cyberattacks growing in sophistication, understanding the threat landscape is the first step toward fortification. According to the Cybersecurity & Infrastructure Security Agency (CISA), phishing and ransomware remain prevalent threats, requiring vigilant detection and prevention strategies.
Building Your Proactive Checklist
Developing a proactive checklist can transform your IT defense strategy. Consider these key components:
- Frequent Risk Assessments: Regular reviews to anticipate and mitigate potential threats.
- Diligent Software Updates: Timely updates are crucial for closing security gaps.
- Stringent Access Controls: Implement least privilege principles to enhance security.
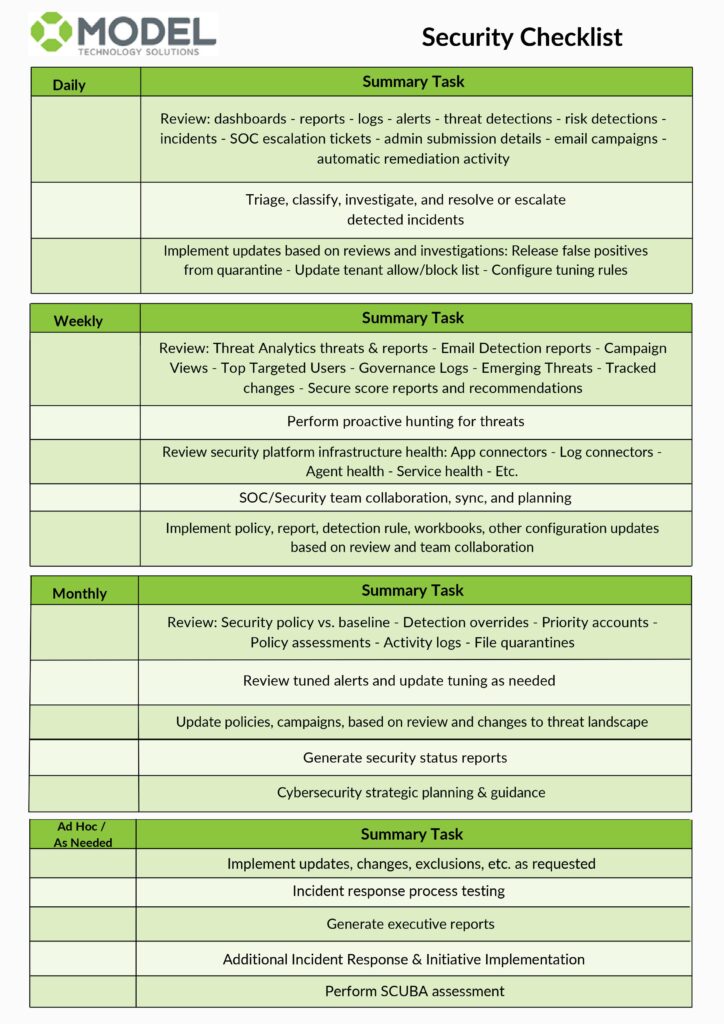
Ongoing, proactive maintenance of security is part of what we do for our clients. Many IT Directors bring us into a co-managed relationship to help alleviate the stress of creating and maintaining an ongoing schedule. We created this security checklist from the regular activities we do for one of our clients using our vCISO portal.
If you’d rather build your own list, start here:
1. Conduct Risk Assessments:
- Evaluate potential internal and external threats quarterly.
- Review and update access controls and security policies.
- Assess the effectiveness of current cybersecurity tools and practices.
2. Ensure Software and Systems Are Up-to-date:
- Implement automated systems for regular software updates and patches.
- Schedule monthly checks for system updates and vulnerability patches.
3. Enforce Strong Access Control Measures:
- Regularly update and enforce password policies.
- Utilize multi-factor authentication for sensitive systems and data access.
- Conduct access reviews every quarter to ensure the principle of least privilege.
4. Incorporate Advanced Threat Detection:
- Deploy intrusion detection systems that use the latest AI technology.
- Monitor network traffic and log data for unusual activities.
5. Train and Educate Employees:
- Host monthly cybersecurity training sessions.
- Send regular updates about the latest phishing tactics and social engineering scams.
- Test employees with simulated phishing attempts bi-annually.
6. Develop a Comprehensive Incident Response Plan:
- Create clear response procedures for different types of security incidents.
- Assign roles and responsibilities for incident response.
7. Test and Improve Security with Simulations:
- Run bi-annual simulation drills for cyberattack response.
- Review and revise the incident response plan based on drill outcomes.
8. Stay Informed and Agile:
- Subscribe to IT security bulletins and alerts.
- Hold quarterly reviews to adapt strategies based on new cyber threats.
Remember, this checklist is a starting point. The evolving nature of cyber threats means that your approach to IT security should be dynamic and adaptable. For a comprehensive, customized checklist suited to your organization’s specific needs, reach out to the experts.
Or, just download our security checklist and make any changes necessary for your org.
Still too much to do and not enough time? Reach out to schedule a consult to see if we might be the right fit to manage it for you.
Regular Security Audits
Security audits are not a one-time event but a cornerstone of regular cybersecurity maintenance. Aligning with NIST guidelines, quarterly reviews ensure ongoing protection against new vulnerabilities.
Model can offer a complimentary light scan prior to engaging on a project or co-managed relationship, to better help you understand your cybersecurity posture. We also provide full NIST cybersecurity assessments with action items.
Advanced Threat Detection Technologies
Invest in advanced technologies for real-time monitoring and preemptive threat neutralization. These systems are vital for staying ahead of cybercriminals.
Threat detection has transcended traditional methods, now harnessing the power of cloud computing and intelligent security analytics. Model Technology Solutions’ M365 as a service incorporates Microsoft’s cutting-edge security features, offering a robust shield against cyber threats. This service ensures real-time monitoring and advanced threat detection capabilities, thanks to its suite of security tools and features such as:
- Microsoft Defender for Endpoint: Providing enterprise-level threat detection and response capabilities, harnessing the power of advanced heuristics and machine learning.
- Azure Identity Protection: Leveraging AI to detect and remediate identity-based risks, enhancing the security posture of your access management.
- Advanced Threat Analytics (ATA): Analyzing, learning, and identifying normal and abnormal entity behavior to catch malicious attacks before they cause harm.
Incorporating such advanced tools into your security checklist elevates your proactive stance, allowing you to stay ahead of the curve in threat detection and response.
Employee Education and Awareness Programs
Continuous staff training on the latest phishing and social engineering tactics is vital. Programs endorsed by the SANS Institute significantly reduce human error-related breaches.
Response Planning and Simulation
Effective incident response plans are tested and refined through regular simulation exercises, ensuring your team’s preparedness for any eventuality.
Continuous Improvement and Adaptation
Stay abreast of security trends and integrate new insights into your strategy. It’s a continuous loop of learning, implementing, and refining.
Your cybersecurity checklist is a living document, as vital as any other tool in your IT arsenal. And while internal vigilance is paramount, the complexity of today’s cyber threat landscape can overwhelm even the most skilled teams. That’s where Model Technology Solutions steps in. Our co-managed IT services offer the expertise and support to not just complete your checklist but to elevate your cybersecurity readiness. Let’s secure your operations together, ensuring your focus remains on high-priority support for your org.
Don’t forget to download our checklist, and reach out if we can be of help.
