Hello, and welcome to Model Technology Solutions’ approach to Unified Endpoint Management.
Today we are talking about Security Level 4 of our maturity model. If you’ve missed the introductory video or any other video in this series, you can find them linked from our webpage at model-technology.com/uemmaturity.
The topics we’re going to cover in today’s post are:
- What is Unified Endpoint Management?
- Our Maturity Model Phases and Categories
- Endpoint Security Level-4 Overview
What is Unified Endpoint Management?
The standard definition of Unified Endpoint Management is…
…a single platform for management of devices such as phones, tablets, and desktops supporting many different use cases.
At Model Technology Solutions, our definition expands on this a little bit.
Model’s Definition: A collection of processes supported by technology for the management of devices such as phones, tablets, laptops, and desktops supporting many different use cases coupled with well-defined processes, molded to your organization’s security and application needs, to enable productivity while reducing potential security risks.
Our definition, in addition to the platform, also includes processes that take into account your organization’s security needs, application needs, and personas. The ultimate goal of Unified Endpoint Management is to enable productivity while reducing any potential security risks and minimizing costs, and the processes that you implement are as much a part of that as the platform that you use.
Our Unified Endpoint Management Maturity Model
Our unique maturity model combines elements that we classify as the Unified Endpoint Management maturity categories with five “phases” for each. These phases all have a variety of characteristics that define them. These phases are not new; we did not make them up. They are something that our industry uses pretty frequently.
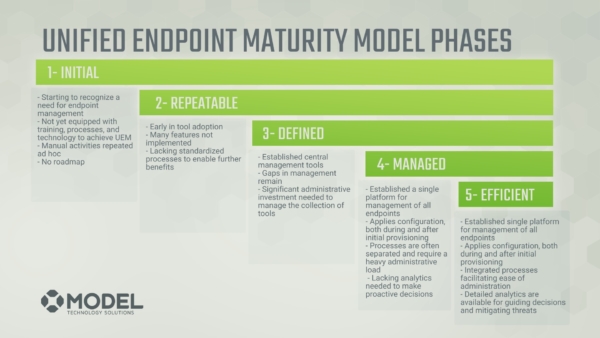
Our maturity model also includes five categories which the phases can be applied to rate. This is our own spin on the maturity model, but it’s this kind of specification that makes our model significantly more useful than with just the generic phases.
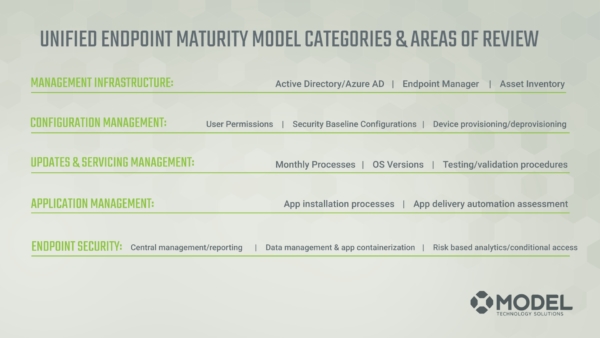
Here are the maturity model categories as they pertain to Unified Endpoint Management.
- Management Infrastructure: Active Directory/Azure AD, Endpoint Manager, Asset Inventory
- Configuration Management: User Permissions, Security Baseline Configurations, Device Provisioning/Deprovisioning
- Updates and Servicing Management: Monthly Processes, Operating System Versions, Testing and Validation Procedures
- Application Management: Everything from App installation processes to App delivery automation assessment based on personas. For example, assessment that says “If you’re this kind of person in this kind of role in the organization, you get these kind of applications.”
- Endpoint Security: Central Management/ Reporting, Data Management and App Containerization, Risk Based Analytics, and Conditional Access Policies.
The goal of the maturity model is to assess where you and your infrastructure are in each one of these five categories. To do so, we take the categories and apply the phase or maturity level that you’re in to each of them. This gives a pretty accurate summary of how “mature” your infrastructure is plus leads to actionable steps for how to improve.
⦁ Defender for Cloud Apps
⦁ Defender for Endpoint
⦁ Defender for an identity
⦁ Different Alerts
⦁ Security Scores
⦁ Session Alerts
…and make recommendations for how you can best improve your infrastructure security based on our findings. In the area of remote endpoints and cybercrime, it’s super helpful for getting some perspective about your infrastructure and identifying areas to improve your security.
Click here to learn more if you’re interested in a maturity model assessment.
If you have any questions, you can find me at jason.rutherford@model-technology.com.
Level 4 Endpoint Security
In this series of posts, we’re exploring what each of these categories looks like at each of its respective phases. And today we’re going to be discussing Level 4 Managed of Endpoint Security in depth. To read about Endpoint Security level 3, you can see last month’s post here.
You’ll also find that endpoint security branches out into organizational security as well, so you can also apply some elements of this maturity level to that focus as well.
Level 4 Endpoint Security is the “managed/capable” state, which means that regarding Unified Endpoint Management maturity you’re doing quite a few things right. For example, in this phase:
- Centralized Security Tools are integrated into the endpoint management and provide easy identification of your security posture and the state of enforcement for those requirements.
- Application-level Management is deployed and helps to secure access to organizational resources and otherwise regulates unmanaged endpoints.
- User Authentication requires Multifactor Authentication reduces the risk of compromised credentials that expose the organization to threats.
- Conditional Access/ Session Controls are in place to restrict resources or change how resources behave based on certain conditions of the user and device.
- Analytics are available even if they are not actively being monitored or having any action taken on them.
Now let’s take a look at specific examples of each of these features.
Centralized Tools
Having a centralized, sophisticated set of tools that you’re using to control and monitor the state of the endpoints is a component of a security Level 4. Some notable options include:
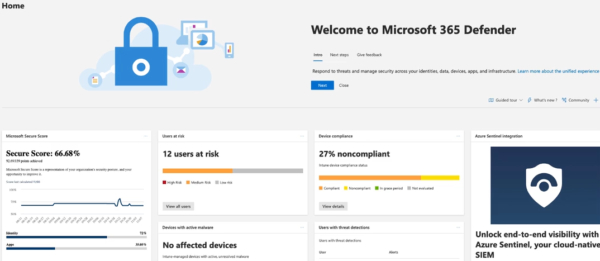
Microsoft 365 Defender which aggregates the different Defender components into a single dashboard.
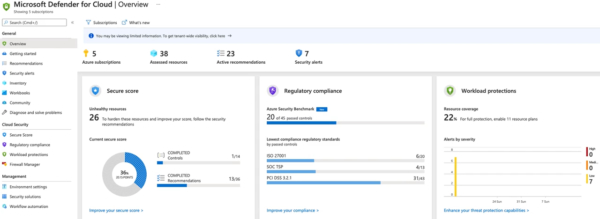
Defender for Cloud takes different components like firewall, regulatory compliance, and gives you a secure score against all your Azure resources.
Defender for Cloud Apps aggregates your shadow IT session controls and discovered applications. These apps look at all the different areas to provide a single console or single pane of glass product.
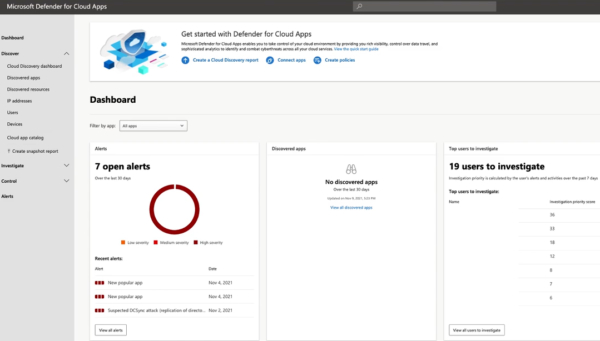
Each of these programs is a Microsoft example of centralized security tools that allow for more-capable management of endpoint security.
Application-Level Management
Application-level management means that you are able to identify and manage different endpoints in different ways according to their status. Elements like:
- App discovery
- App isolation
- Tagging or classification
- Alerting
…are all examples of what application management tools look like at Level 4. This isn’t limited to applications that are installed on devices or endpoints. SaaS or service-based applications like ServiceNow are also great examples of this.
Here’s an example of a compliance dashboard alert that we received from a user that had an unusual addition to credentials on our ServiceNow app.
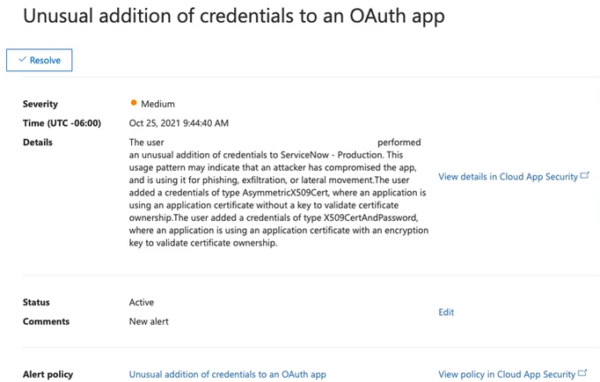
Having an alert for an unusual addition of credentials on an OF application to an approved application requires maturity in your security stack. It provides valuable information as it pertains to the endpoints. That’s why this element is rated as a part of level 4 in endpoint security.
Conditional Access and Session Controls
Another important component of Endpoint Security Level 4 is enforcement of data access policies such as guest accounts or trusted versus non-trusted devices.
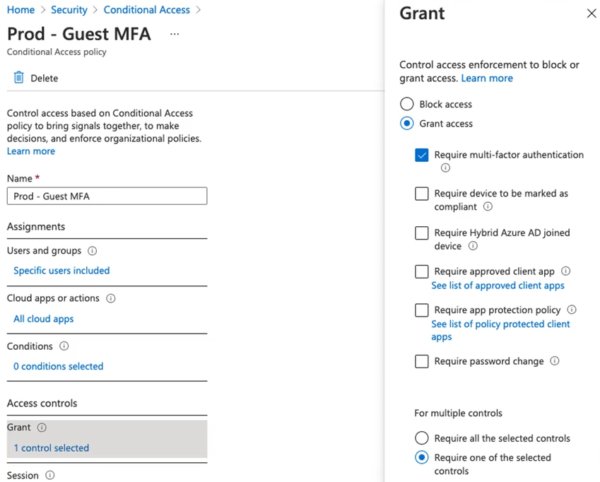
Here’s an example of a production MFA guest account that’s going to require the Grant or it’s going to allow the Grant Control after multifactor authentication has been satisfied.
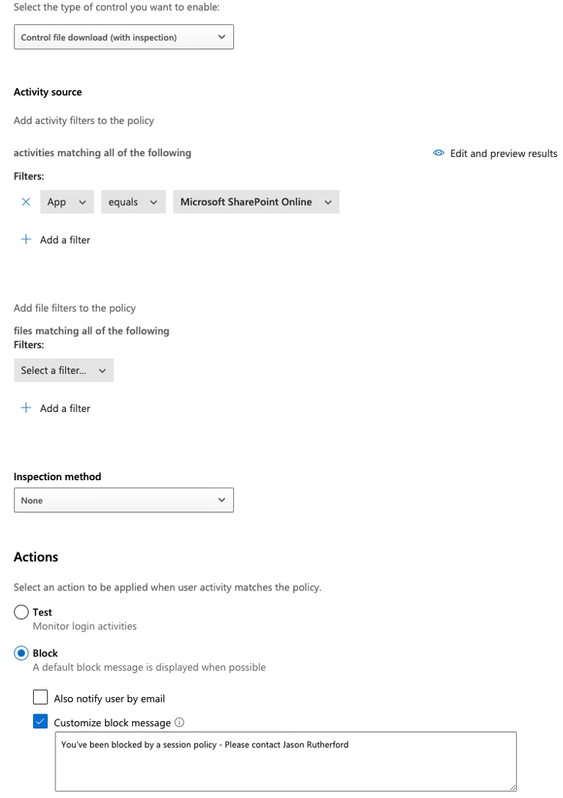
Another great example is using the Microsoft Cloud Access Security Broker (now the Microsoft Defender for Cloud Apps) to leverage conditional access control. These products interrogate the state of the device and determine if the device is secure. Then home devices or other untrusted devices will be kicked over for session controls to block access to certain functions such as downloads from SharePoint online.
Even if a user has full control to SharePoint online in regular circumstances, if they use a home machine (e.g. a less secure access point) to access their SharePoint online, we want to know and block the download.
Analytics
Analytics are also a huge part of level 4 Endpoint Security. In a Level 4 categorization, analytics exist and the data is available as needed, even if the analytics are not fully monitored or utilized very much. For example, here is another dashboard from our cloud app discovery.
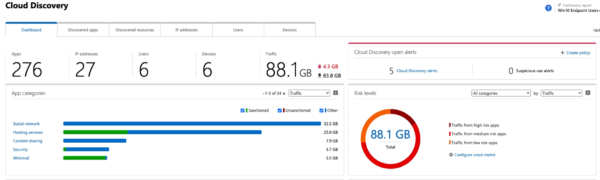
You can see all the apps, IP addresses, and users we’ve discovered. In the top right you’ll also notice that this is based on Windows 10 endpoint users, which is why this is part of the the Unified Endpoint Management maturity model.
Overall, in a Level 4 managed capable state, you’re pretty advanced in your tools and their implementation. Plus you’ve got analytics that you can go tap into when needed, for example, to troubleshoot something once a problem is identified. Level 4 is a great place to be with Endpoint Security. Being there significantly reduces your risk for a data breach, improves monitoring, plus it provides you with the ability to make data-backed decisions related to security.
Our Maturity Assessment
Now, we realize that all of this is a little bit like drinking from a fire hose. Likely you still might be wondering, “Where exactly is my infrastructure regarding it’s maturity, and what would be the next step to improving it?”
This is something we hear quite a bit from our customers. Which is why we have created and are now offering a Maturity Assessment to help organizations like yours get granular precision about your infrastructure maturity.
The assessment essentially rates your infrastructure where it currently is plus gives a plan of how to get to the maturity you want it to be.
Practically the assessment consists of is two 90-minute sessions and a pre-meeting questionnaire to fill out. During the first assessment, we will gather information which will allow us to assess which phases you’re in and how to get to the next phases. From this information, we’ll prepare a findings and recommendations report that will give you the next step in each category as it pertains to Unified Endpoint Management.
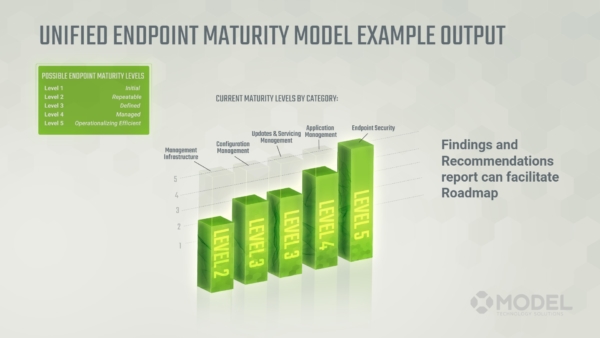
In this report we will also provide high-level yet actionable steps that you can use to move your organization toward a more mature Unified Endpoint Management service.
Concurrent with this, we’re also offering a Microsoft Defender assessment if you’re particularly worried about endpoint security. During this assessment, we’ll review your:
⦁ Defender for Cloud Apps
⦁ Defender for Endpoint
⦁ Defender for an identity
⦁ Different Alerts
⦁ Security Scores
⦁ Session Alerts
…and make recommendations for how you can best improve your infrastructure security based on our findings. In the area of remote endpoints and cybercrime, it’s super helpful for getting some perspective about your infrastructure and identifying areas to improve your security.
Click here to learn more if you’re interested in a maturity model assessment.
If you have any questions, you can find me at jason.rutherford@model-technology.com.
