Welcome to part one of our series on Unified Endpoint Management!
- Do you ever worry about endpoint security?
- Are you worried that there may be cracks in your endpoint management strategy that could increase the likelihood of a data breach?
- Would you like to see how you could improve your infrastructure efficiency while reducing costs and manhours?
Unified Endpoint Management is one possible solution, and the first step in resolving these questions is identifying unseen issues and opportunities for improvement in your infrastructure.
In this series, we’re going to introduce the categories of our infrastructure maturity model “roadmap”. This roadmap is our model for analyzing client infrastructures and knowing the optimal areas for improvement.
In this post you’ll learn about:
-
- What is Unified Endpoint Management?
- Why should you care about Unified Endpoint Management?
- Our UEM maturity model phases and categories.
- An overview of how Model puts all those things together into a cohesive UEM solution that allows you to manage your endpoints and improve your infrastructure.
What is Unified Endpoint Management?
UEM is a single platform for management of devices. Devices could be anything from an Android tablet to an iPhone, an iPad, Windows desktops, Windows laptops, et cetera.
The standard definition of UEM is as follows:
A single platform for management of devices such as phones, tablets, laptops, and desktops supporting many different use cases.
At Model, we take that definition and we expand upon it a little bit:
A collection of processes supported by technology for the management of devices such as phones, tablets, laptops, and desktops supporting many different use cases coupled with well-defined processes, molded to your organization’s security and application needs, to enable productivity while reducing potential security risks.
We look at the universal definition and add “good, well-defined processes.” It can’t just be any process, it must be molded to your organization’s security and application needs to enable productivity and reduce risk.
Why Should You Care About Unified Endpoint Management?
Why you should care about UEM? The four main reason are:
- Increased Productivity: You want to be able to quickly enable productivity. Whether the devices are inside or outside of your organization, you want to minimize the setup configuration assistance required for those devices. Doing that with a Unified Endpoint Management platform makes things a lot easier.
- Centralized Analytics: You want to be able to define and consume key analytics about your organization, data access, and the devices being used.
- Increased Security: We all want to increase our security posture nowadays with things like application containerization, conditional access policies, and a generally more holistic view of endpoint security management.
- Improved End-User Experience: We want to be able to properly support our workforce. Our workforce has changed drastically over the last year, and being able to support them is a key component for a device management strategy.
What this really means and why we really care about UEM is that we want to:
- Save money
- Save time
- Improve user experience
- Have a unified view of all of our assets in the organization
- Reduce our risk
Management services, you can visit our managed services page.
The Model Technology Solutions Endpoint Management Maturity Model
Our maturity model is five common phases.
- Initial
- Repeatable
- Defined
- Managed
- Efficient
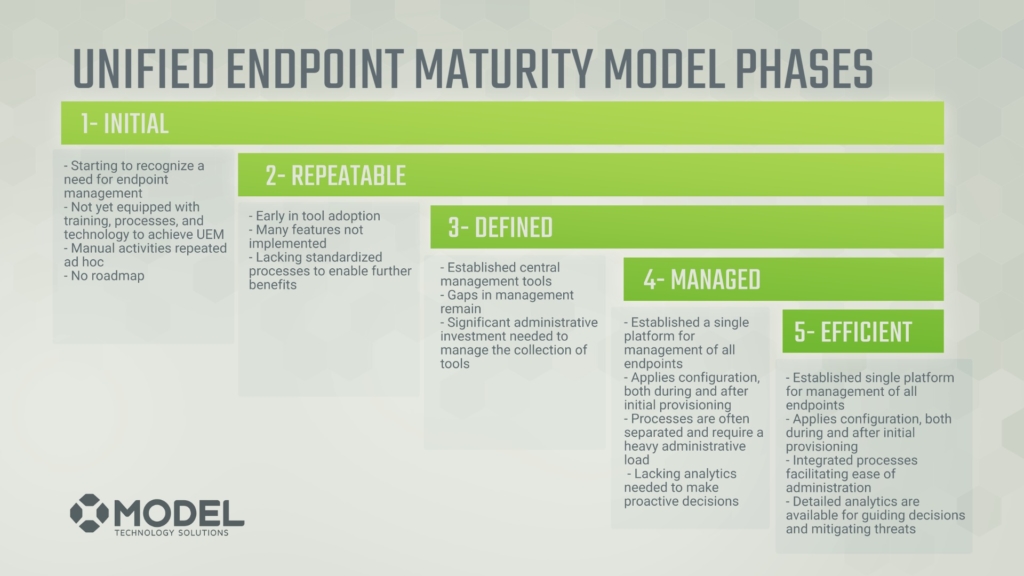
In this series, we’re going to go through those phases with a fine-tooth comb. No matter what phase you’re in, whether you’re just starting to recognize a need for technology, early in a tool adoption state, wanting to minimize overhead management of a central tool you’re already using, missing key analytics, or you’re at the efficiency stage and ready to continue growing, you’ll learn where you are and what’s possible through Unified Endpoint Management.
The Five Categories of UEM Device Management
What really sets our infrastructure maturity model apart is how each of those phases are broken down into five different categories of unified endpoint device management.
- Management infrastructure
- Configuration management
- Updates and servicing
- Application management
- Endpoint security
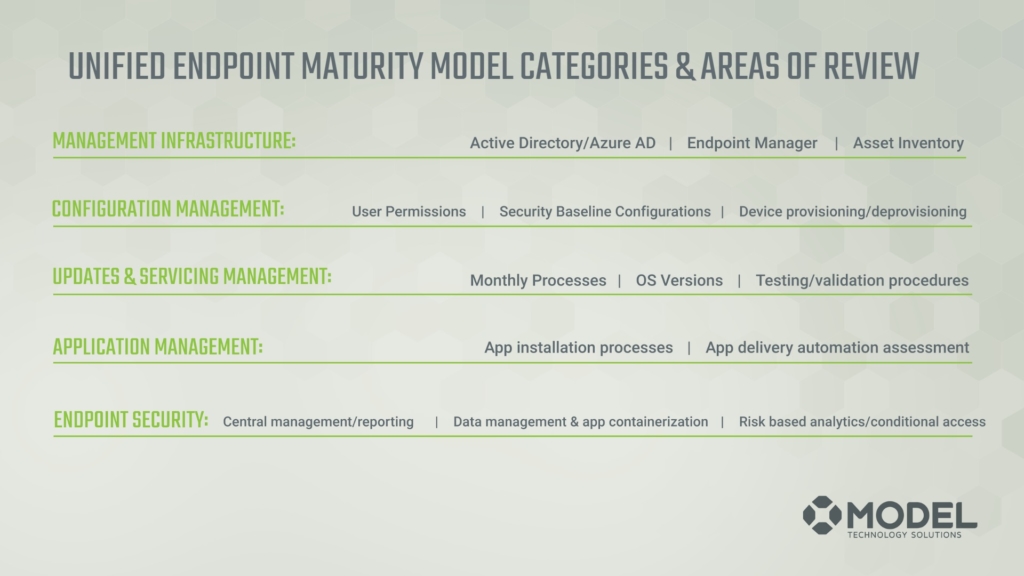
These five phases are what this series is really going to spend some time diving into.
The Model Technology UEM Infrastructure Analysis Roadmap
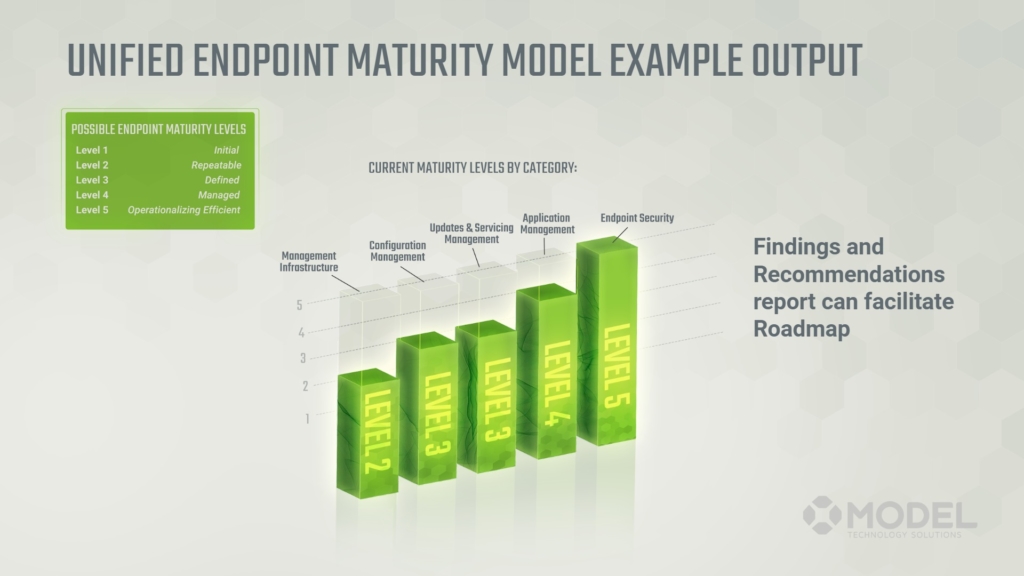
Would you like to know how your infrastructure rates in each of these categories and phases? As a form of output from a roadmap engagement, we offer a free analysis of your five phases for what level they’re at across the roadmap and maturity model. Out of that comes a findings and recommendations report, which will enable you to identify:
- What is the most significant impact to my organization if I focus time and energy on this next?
- What is going to drive my organization further faster?
What Will You Learn/Gain From A Personalized UEM Roadmap?
Things that you’ll learn about through following this coming blog series and, if you’re interested, your own personal roadmap assessment is information about proper management in areas such as:
- Co-management with Intune and endpoint manager on-premises
- SCCM
- Exposing internal applications using Azure Active Directory, coupled with config-manager and app configuration policies deployed to mobile devices to be able to really expose some of those internal applications externally
- Control access with Intune
- Conditional access
- Risk-based conditional access policies
- Security models from Microsoft
- All the different elements when they’re put together in a cohesive, unified endpoint management solution
A “Single Pane Of Glass” Endpoint Management Solution
One of the other end results of a well-defined Unified Endpoint Management infrastructure is the ability to look at aggregated data from multiple sources on a single platform, which Model Provides. For example, pulling information from:
- Software updates, whether they’re from Intune, SCCM, or Windows updates
- Log analytics or from a defender for mPoint
…then being able to aggregate all of this data into a dashboard is something we’ll talk about more later in the series when you get to those most-efficient states.
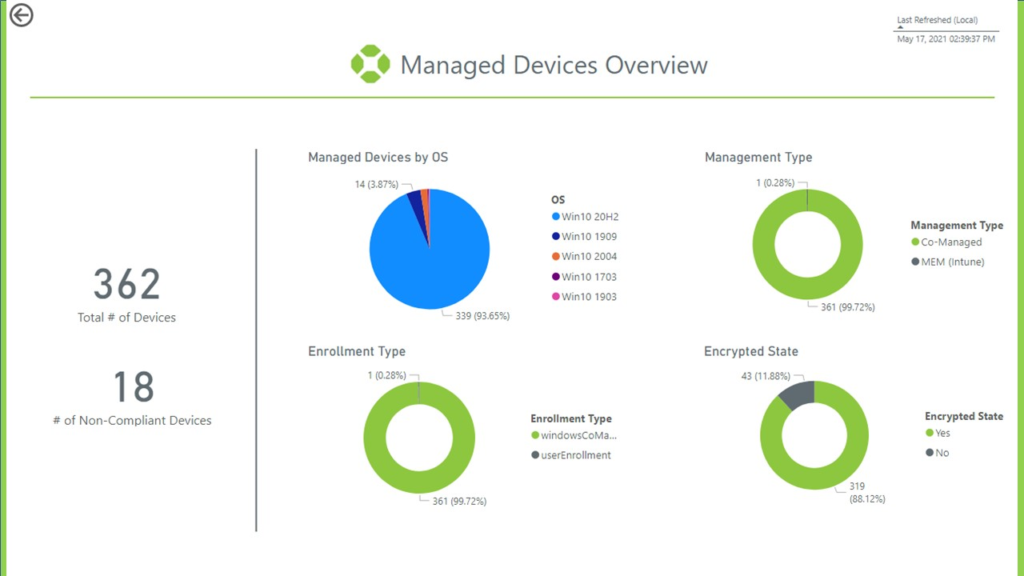
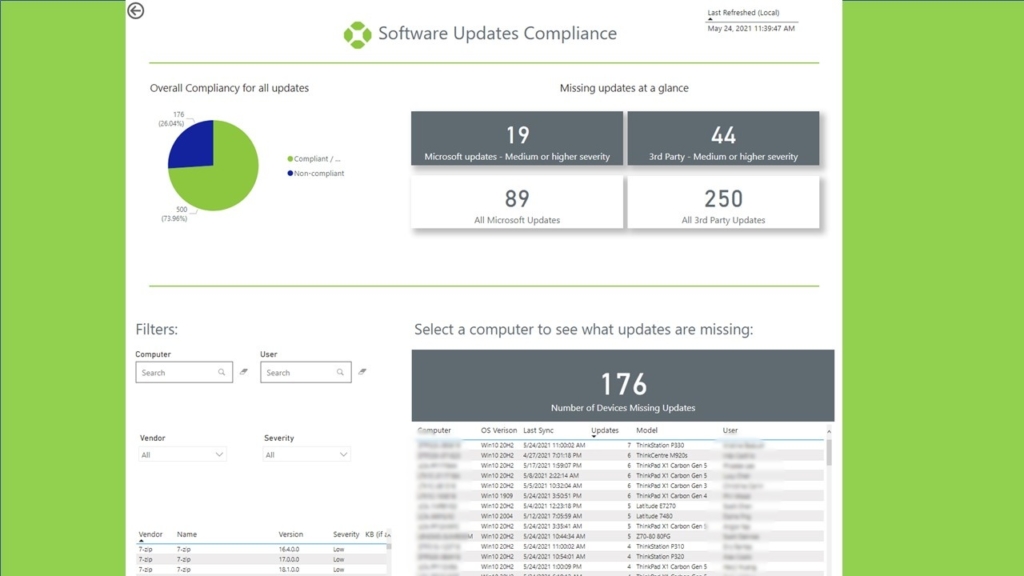
Our Azure line of tools out of our IP division enable you to have additional insights into operating system deployments. For example, Azure allows you to have granular control over when things are executing on your machines from an end user’s perspective or more options for a dynamic deployment within the walls of your infrastructure for something like SCCM.
We’re going to go through each level of every category in some level of detail to help you understand how we approach Unified Endpoint Management.
If you’d like to come along with is in this series, be sure to subscribe to our email digest! And if you’re interested in learning more about our Unified Endpoint Management services, you can visit our managed services page.
