For most companies, gone are the days of simple cybersecurity and endpoint security solutions. With the increased complexity of remote work and rapidly shifting cyber threats, dedication and focus are now required to protect your environment from modern threats.
A Chief Information Security Officer (CISO) provides direction and dedication for your cybersecurity and endpoint security management efforts. However, many companies need this focus immediately and may not have the resources available to hire someone to fill the role. It can take months to find the right candidate, and these kinds of professionals are in high-demand, making them difficult to find and expensive to hire.
Model Technology Solutions recently launched our vCISO offering to help companies in this predicament. The vCISO gives companies who need the cybersecurity direction and expertise of a CISO but don’t have the time or resources available to hire a full-time professional to fill the role. Or, they’re just looking for someone to fill the gap until they hire.
As a whole, the offering includes:
- A comprehensive NIST-based cybersecurity assessment that helps you to discover cost-effective projects you can undertake to improve your cybersecurity
- Access to the Model vCISO portal where you can continually update and re-assess your environment as you make changes, and where you can watch your cybersecurity posture improve
- Monthly vCSIO meetings with Model’s expert cybersecurity director who will help you to reassess and redirect your efforts to get the most return out of your resources and adapt to changes in the cybersecurity landscape
In today’s post, were going to talk about the vCISO Portal security tool that comes as a part of this offering. We’ll cover how this tool helps you from onboarding, through assessment, all the way to providing downloadable reports. This portal gives you one centralized location for all your vCISO needs, helps you to improve your cybersecurity cost-effectively, and even provides reports you can use to reduce your premiums and prove your cyber-readiness.
Onboarding and Questionnaires
Onboarding in our cyber security program is quick and easy. With dynamically generated questionnaires and auto-generated action plans in the form of policies, we can quickly scan external assets for vulnerabilities and track our cyber cybersecurity posture score and benchmarks.
The onboarding questionnaire is general in nature and reflects the high level architecture of your organization with different categories.
Cybersecurity Action Plans
Once the onboarding is complete, we can move into our action plans.
To see the action plans, go to assessments in the portal. Your action plans are based off of industry standards and regulations that you must comply with.
This is an example of a healthcare based organization, so the action plan is based on NIST-based controls and HIPAA compliance frameworks. These options give you about 20 or so sections to assess.
Results
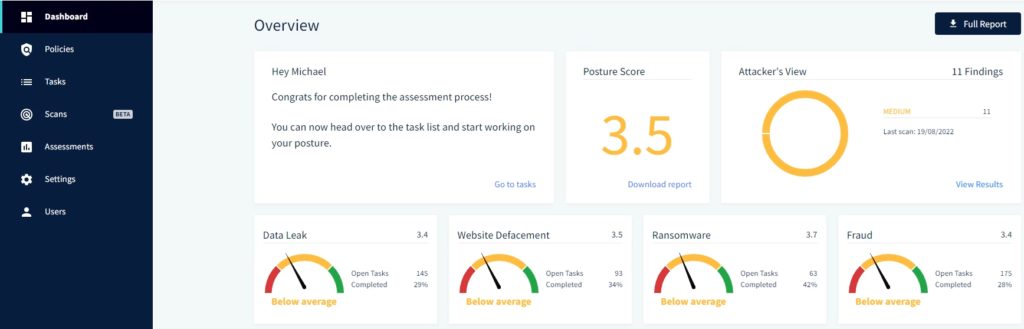
Once all the assessments are complete, the dashboard is then populated with your assessment and scan results. You can see your current status and what your priorities might be for improvement.
The scores profile lists all the different sections in which you have assessed in your environment. The dark blue section shows your current score, while the light blue is your target score.
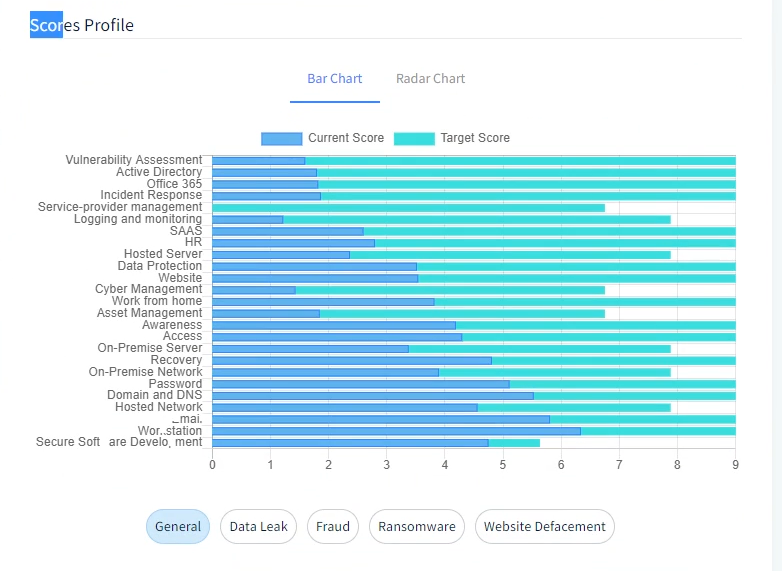
For instance, if you look at active directory you can see that the current score is 1.8 and our target score is nine.
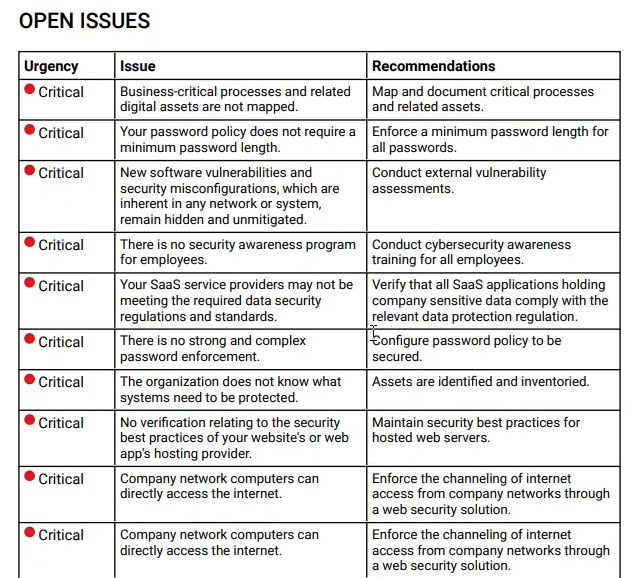
Cybersecurity Tasks and Severity
When you’re ready to improve that active directory score, you click on tasks. Then to make things easier to see, you can filter that policy down to active directory.
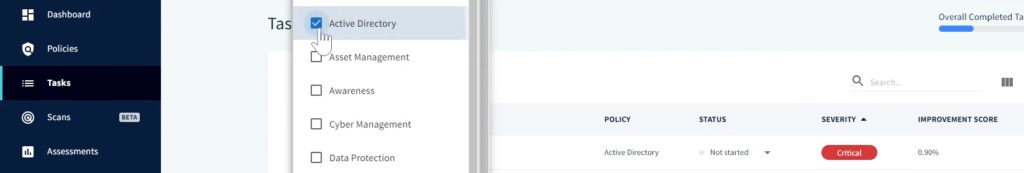
Once everything is filtered and sorted by severity, you can see that there few critical ones. Today we’ll take a closer looks at at disabling SMBV1.
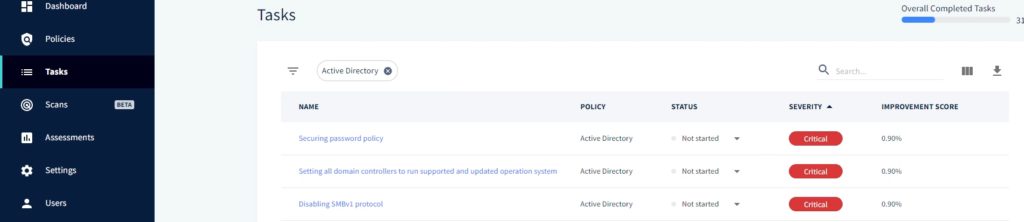
Once you open it up, you can see that SMBV1 is extremely vulnerable with many exploits.
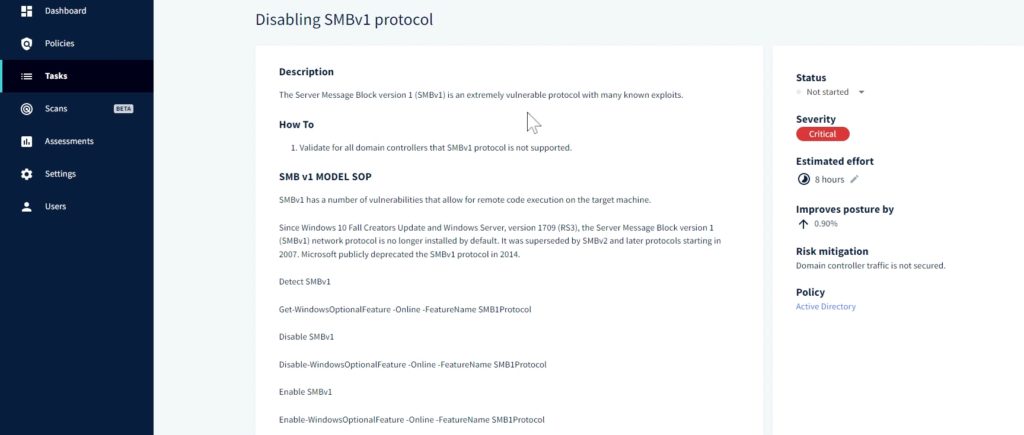
As part of this control, we provide a standard operating procedure to get a detection or disable that feature. Set this to “in progress” and get a change control request ready for deployment.
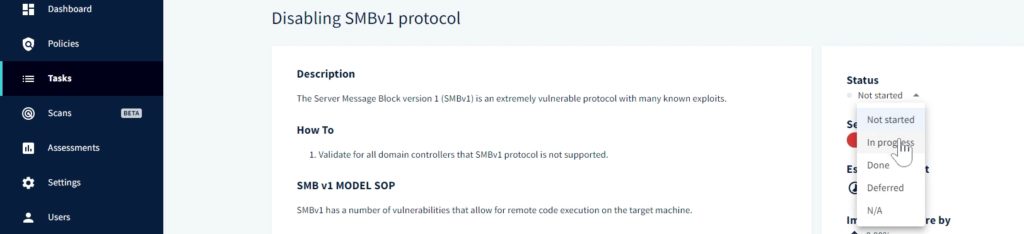
Once again on the dashboard, you can also look at the task progress.
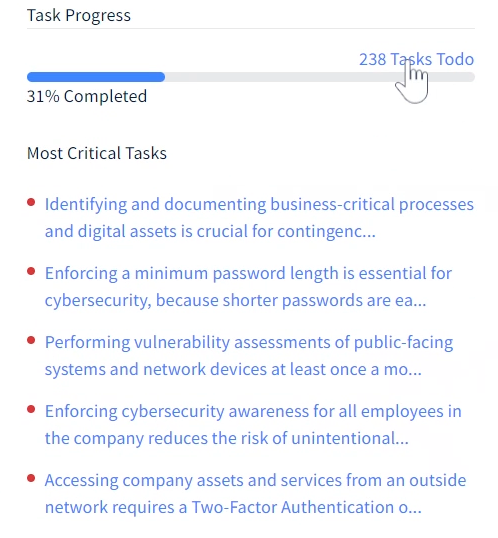
This dashboard shows 238 tasks that need to be done. This is quite a long list, but you can again filter it down by policy, workstation, etc.
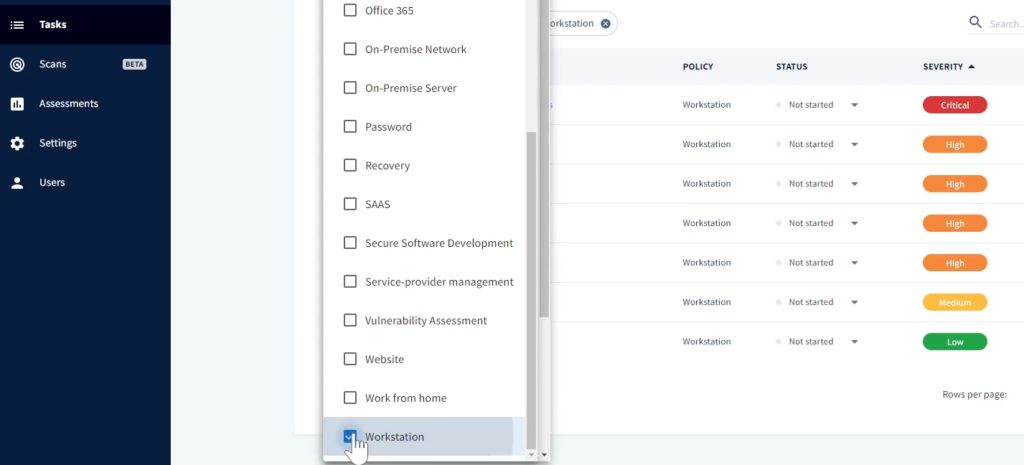
Downloadable Cybersecurity Reports
The last thing we’re going to go over today is a full report that can be downloaded from the portal and shows your progress against the different systems and controls that you’ve been putting in place to improve your score. This report is perfect for sharing with senior leadership. It gives all the different details about your current score against your benchmarks…
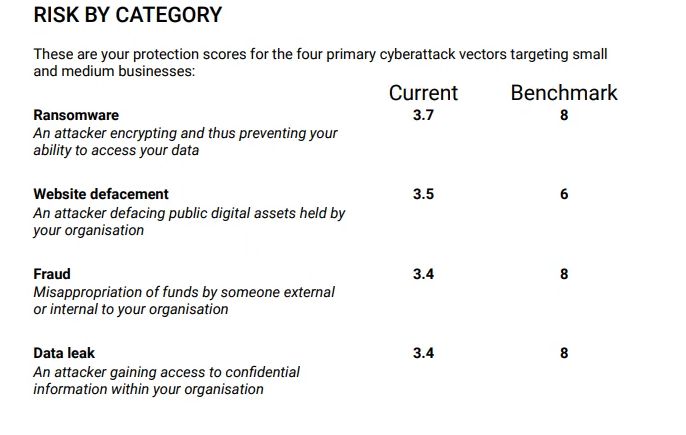
…radar charts and scan summaries…
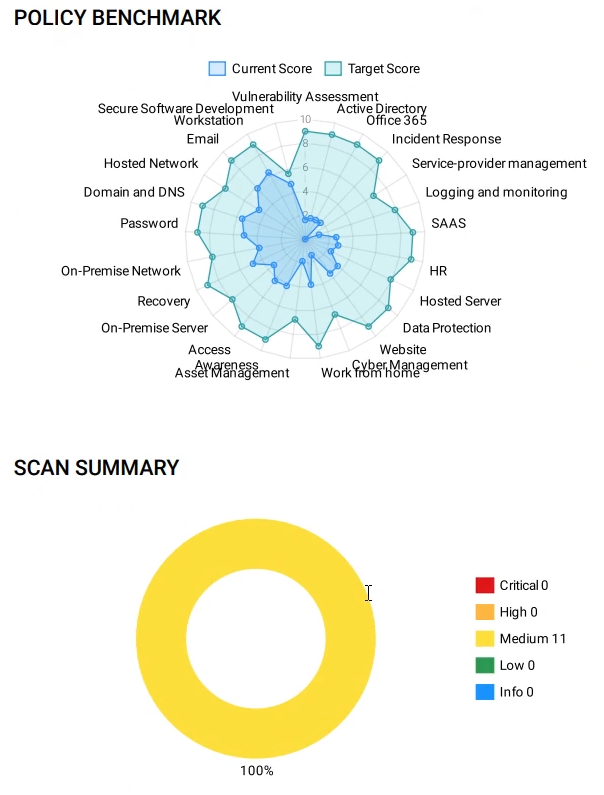
…and critical high, medium, and low scores.
As a part of our vCISO offering, you’ll have access to this portal for twelve months to track your progress on your cybersecurity program. You can also leverage our expertise to help accelerate your cyber operations.
Start Your NIST-Based Assessment Today
Do you want to improve your cybersecurity and endpoint security management as cost-effectively as possible? Would you like to reduce your insurance premiums? The first step step is to assess your environment and benchmark where your security is currently.
Our NIST-based cybersecurity assessment will help you do exactly this. As part of the assessment, we assess your environment against a broad spectrum of controls to:
- Benchmark your cybersecurity
- Identify unseen holes in your protection
- Provide cost-effective action plans
You can use this information to decide which projects will give you the best return for the least investment, and you can also prove your cyber readiness to cybersecurity insurance providers, possibly reducing your premiums.
As a part of purchasing, you’ll also get access to our full vCISO offering for a year to help you to leverage your findings to make real improvements to your cybersecurity for the lowest costs.
You can learn more about the cybersecurity assessment here. Don’t wait until you have a data breach to assess your environment! Start your assessment here with our 12-question onboarding questionnaire today.
