Welcome to Model’s Approach to Unified Endpoint Management. This is the final post in our Management Infrastructure Maturity Model series, which is series of posts and videos we’ve done about our proprietary approach to UEM and the different stages of maturity in the categories of our maturity model. This post will include:
-
- Our running definition of Unified Endpoint Management
- A brief review of our proprietary Maturity Model
- The defining characteristics of Management Infrastructure at a Level 5 Maturity
What is Endpoint Management?
Let’s start with definitions. The standard definition of Unified Endpoint Management is…
…a single platform for management of devices such as phones, tablets, and desktops supporting many different use cases.
At Model Technology Solutions, our definition expands on this a little bit:
Model’s Definition: A collection of processes supported by technology for the management of devices such as phones, tablets, laptops, and desktops supporting many different use cases coupled with well-defined processes, molded to your organization’s security and application needs, to enable productivity while reducing potential security risks.
Our definition, in addition to the platform, also includes processes that take into account your organization’s security needs, application needs, and personas. The ultimate goal of Unified Endpoint Management is to enable productivity while reducing any potential security risks and minimizing costs, and the processes that you implement are as much a part of that as the platform that you use.
The UEM maturity model
We developed this maturity model from existing phases to help our customers benchmark the maturity level of their organization, especially as it pertains to their endpoint devices.
The phases included in this model are:
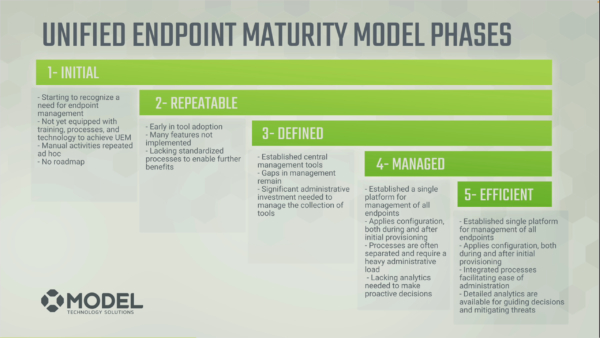
- Initial
- Repeatable
- Defined
- Managed
- Efficient
These phases range from starting to recognize a need for endpoint management, all the way to a highly-mature solution that utilizes:
- A single platform
- Managed configuration
- Pre and post provisioning
- Integrated processes
- Driving your decisions based on analytics
…in their environment.
Then, within these phases are 5 Categories, including:
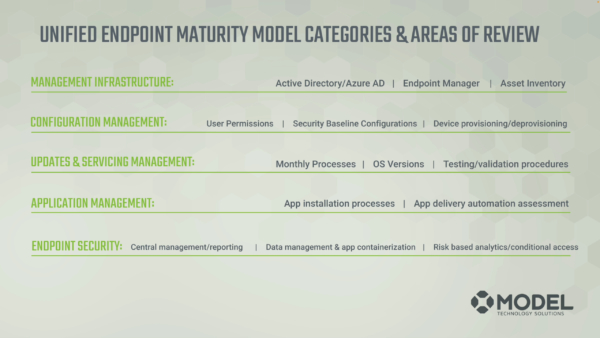
- Management Infrastructure
- Configuration Management
- Updates and Servicing Management
- Application Management
- Endpoint Security
Each one of these categories has a video and blog discussing their Level 5 characteristics, with the exception of Management Infrastructure which we’ll cover today. To get a full understanding of what it means to be at a level 5 in all areas of endpoint management, you can find the Maturity Model videos playlist on YouTube here, or find previous posts from the series on our blog. Also be on the lookout for our ebook coming out soon about the “gold standard” for Level 5 maturity across the board.
Management Infrastructure Level 5
Okay, let’s jump into Level 5 Management Infrastructure. When reviewing the maturity level your organization’s Management Infrastructure, there are some key attributes to look for.
The first is that all your end points are joined to a central directory and are accessed using directory-managed credentials. This might seem like an over obvious topic, however, when you start thinking about your organization and all the different elements that are a part of it, ensuring that all credentials and all devices are managed from a directory, including mobile devices, is important to Level 5 maturity.
Additionally, in regards to that single centralized platform which includes mobile devices, you’re able to contact and manage endpoints connected to any network that has internet connectivity. Essentially, any time you have basic internet connectivity, you’re able to manage those endpoints and get asset inventory information updated. Relying on a VPN to manage devices is not a a characteristic of Level 5 Management Infrastructure.
Next, hardware and software asset tracking is enabled and updated regularly for all the endpoints. This allows centralized reporting of the state, along with automated alerts for proactive management. That is an important component of Level 5 as it pertains to Management Infrastructure.
And finally, processes are established and followed on a continual review to ensure that new features and functionality are in a production use.
Let’s cover each of those items more in depth.
All Endpoints Joined To A Central Directory
Unless there’s a technical reason why certain devices CANNOT join the directory and are unsupported, being in Level 5 would have all of your elements in one directory. This is where all your users, groups, and devices live, and it would take into account your total population as well. 
Reasons to ensure users, groups, and devices are managed from a central directory may seem obvious, but reasons for Azure AD as your central directory include global access and control over organizational resources. This enables a level of support for those resources that is otherwise unachievable. Additionally, having all your resources joined enables enhanced security features such as Multifactor authentication. Finally, the a common directory enables a level of logging that would require many hours of design and implementation to achieve on non-connected systems.
Up-to-date Asset Inventory/ Managed and Updated from any Internet Connection
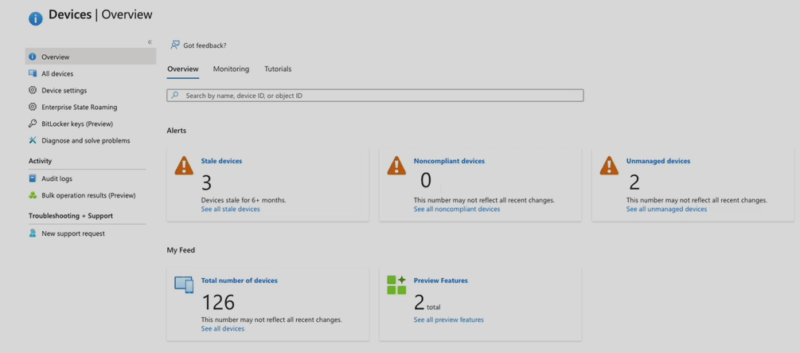
Level 5 also includes an up to date asset inventory and updated from any kind of internet connection. For this kind of solution, you’d see your number of:
- Total devices
- Stale devices
- Non-compliant devices
- Unmanaged devices
…on a very quick dashboard. See the example below of something you might see in a dashboard from Azure AD.
You can take that same tool set and go over into Endpoint Manager (formerly Intune), into the work from anywhere component, and you see what your score would be out of 100 and whether you’re lacking in provisioning, management, identity, or your Windows device is just not capable of being able to work from anywhere. This is also a glimpse into the Analytics that you would have at a Level 5.
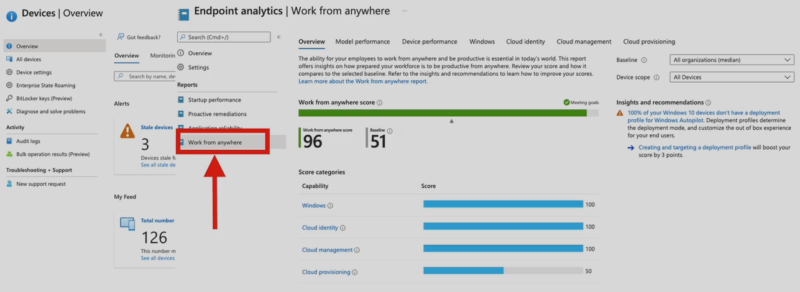
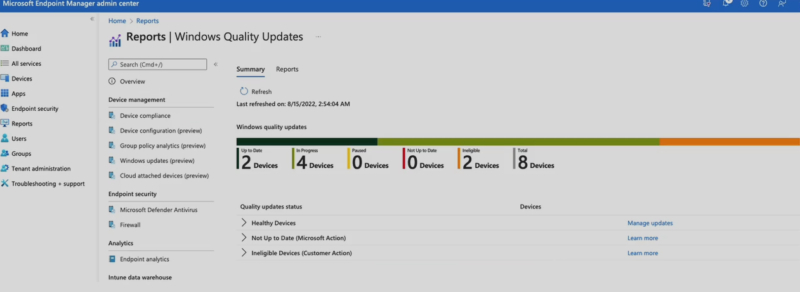
You could also be using software like Microsoft Auto Patch to look at the results of the last test group that you were in. In the example below, you can see the devices that are up to date, in progress, and ineligible. Being able to see those total devices, whether or not they’re on your network, whether they’ve checked in, and where they’re working from is a great example of how you would use this tool set at a Level 5.
Established and Audited Processes
And finally, Level 5 includes stablished processes. These processes need to be established, then also reassessed and reestablished over time.
Here are some examples of processes that would be in place at a level five of maturity in management infrastructure.
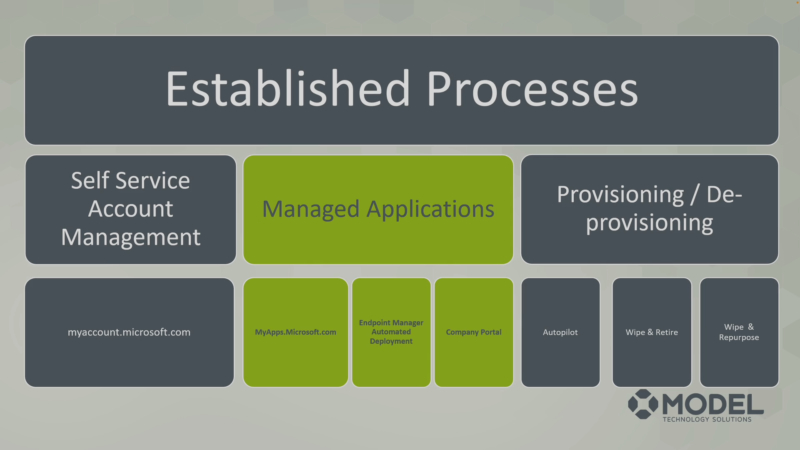
⦁ Self service account management: Anytime a user calls, maybe you put out a memo to your organization saying, “Here’s how you manage your user account on your own, at myaccount.microsoft.com.” This is vital to reducing the call volume pertaining to settings that the end user can manage which reduces their time to resolution. The way to access this feature is to go to myaccount.microsoft.com to find security info, password info, settings and privacy, the organizations you belong to, your sign-ins, your devices, and many other things you can do and interact with.
⦁ Managed applications: This process is all about user enablement and reducing downtime to your user population. Whether you go to myapps.microsoft.com because you are using an SSO configuration from your tenant, you’re deploying the application through Endpoint Manager through an automated deployment, or the user’s going to request a self-service deployment from the company portal, you have a process that’s established and being reviewed frequently.
⦁ Provisioning and deprovisioning: Maybe you’re using Autopilot, or there’s a scenario to wipe and retire or repurpose when a machine’s done. While having a process is the first step, automating those process (where applicable) can reduce time, confusion, and provide a better overall IT service.
Each of these processes are established, defined, then reassessed at specific intervals for the purposes of improving your management. Put all of these different elements together, and you have the baseline for a highly-mature Management Infrastructure in your environment.
Benchmark Your IT Maturity
All of these elements are the essential elements to highly mature Management Infrastructure in your environment. But how do you get there? You need to start with a benchmark of where you’re at then develop a roadmap for where you want to be, and we’d love to help with that. Our IT Maturity Health Check service is a perfect way to assess the maturity of your infrastructure across the board. With this data, you can then identify the best categories to improve and projects to implement in order to improve your maturity, and reap the benefits that result from it in security, compliance, and cost-effectiveness.
Practically what this service looks like is:
- A short questionnaire
- A 90-minute onboarding
- A 90-minute review session
Our first 90-minute session will help us get a deeper understanding of your environment. We’ll review everything from business operations, alignment, challenges, roadblocks, user adoption of new technology, and talk about specifics of where you’re at from a technical and a tactical standpoint in each of the categories.
Using your questionnaire and the information from this session, we’ll create a findings and a prioritized recommendations list that we’ll deliver in the next 90-minute session. You will also have the opportunity to ask any questions about how we operate or about the report. The information delivered during the second session will help you identify projects you could use to improve your maturity.
If you’d like to learn more about the Health Check, you can follow the links in this paragraph. Many of our current clients have gone through the Health Check and found it to be a tremendous value.
Questions? Feel free to reach out! You can use our contact page, or you can email me at Jason.ruthford@model-technology.com. Always happy to chat!
