Recently, we were given the task to monitor multiple machines in untrusted domains using SCOM. However, there were not enough machines to justify standing up a gateway server for each environment. Therefore, we simply relied on leveraging the already existing PKI infrastructure in the domain in which the Management Servers reside to monitor manually installed client agents in untrusted domains.
Below are the steps we followed in order to get this done. This guide assumes you have working knowledge regarding how to access the CA console, as well as import and export certificates. We also assume that there is some routing set up to enable name resolution between environments. (NOTE: ensure that TCP port 5723 is open both ways between the target server and the Management Server, and your Certificate Authority needs to be configured for HTTPS).
Creating a Root Certificate
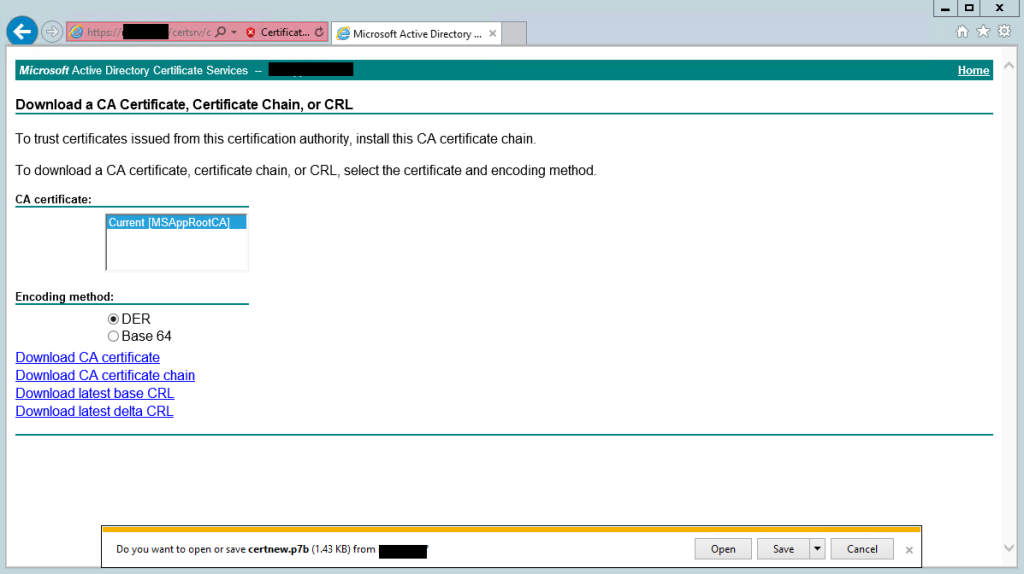
1. On the Management Server, navigate to the certificate server using a web browser (typically https://<certificate server/certsrv) and select “Download a CA certificate, certificate chain, or CRL”
 2. Select “Download CA certificate chain” and save it as certnew.p7b
2. Select “Download CA certificate chain” and save it as certnew.p7b
3. Import the cert into the Trusted Root store of your Management Server
Creating an OpsMgr Certificate
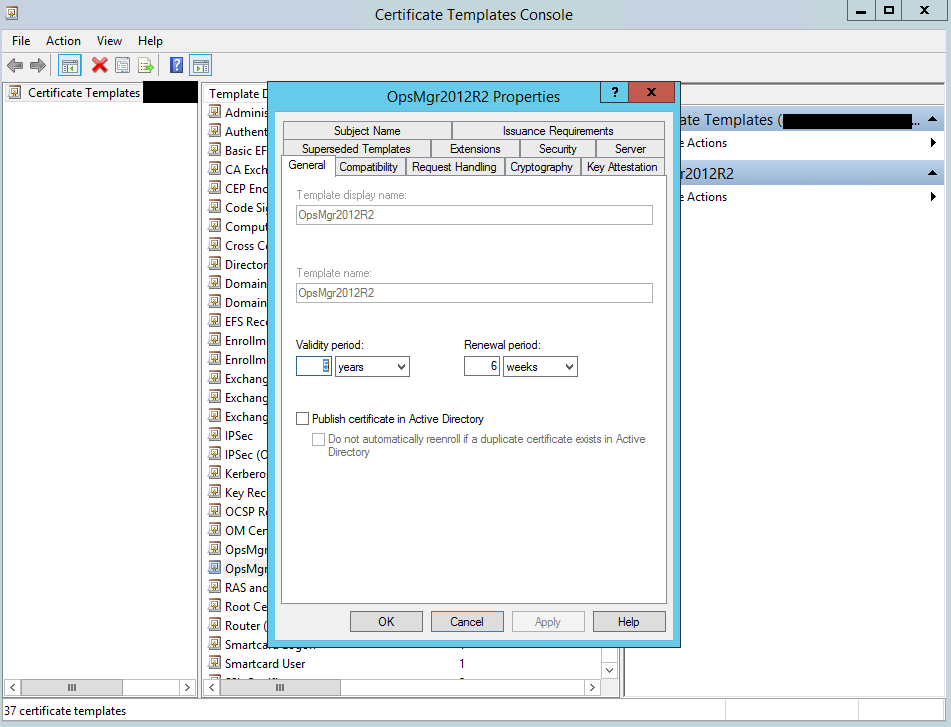
1. In the CA console, right-click Certificate Templates and select Manage
2. In the Certificate Templates Console, right-click Computer and select Duplicate (in this example, we simply leave the compatibility settings to Windows Server 2003)
3. On the General tab, name your template
4. On the Security tab, grant Enroll and Autoenroll permissions for:
- Authenticated Users
- Domain Admins
- Domain Computers
- Enterprise Admins
Import the OpsMgr Certificate to Management Server
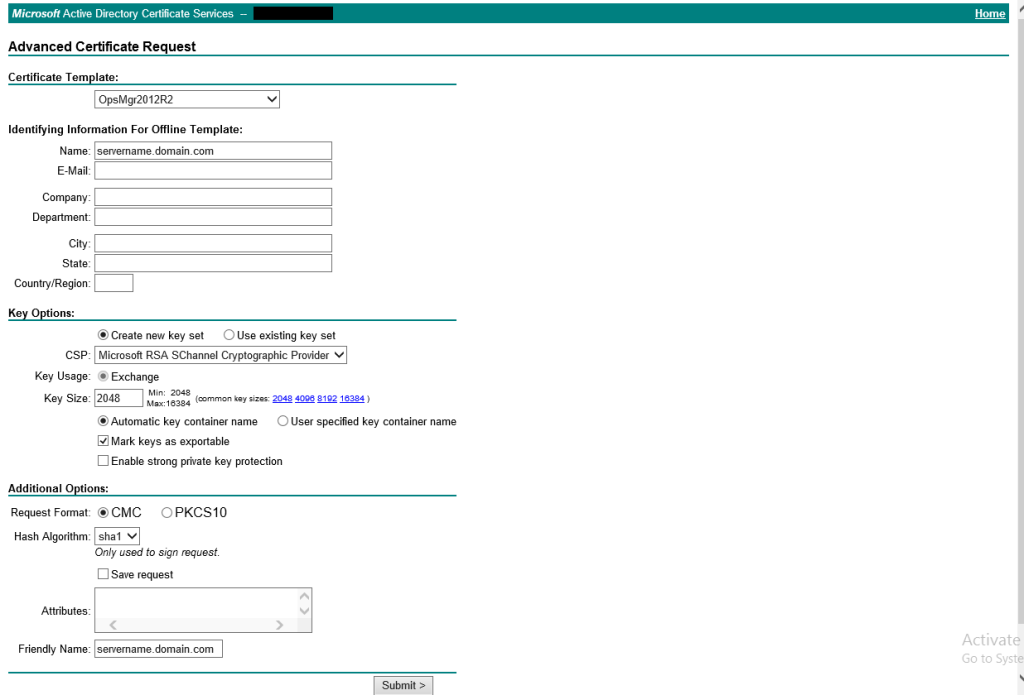
1. On the Management Server, request a certificate using an advanced certificate request, creating and submitting the request to the CA
2. Select the template and enter the FQDN of the Management Server in the Name and Friendly Name fields
3. Submit the request and install the certificate
NOTE: The certificate will now be in the personal store of your user profile! Navigate to that location using the certificates snap-in in the MMC and export the cert, along with the private key, to a location on your hard drive.
1. After this cert is exported from your user personal store, import it to the personal store of the Management Server
Import OpsMgr Certificate to Monitored Server
1. From the Management Server in the trusted domain, follow the same process in the previous section to request a cert, only use the FQDN of the machine you wish to monitor
2. After exporting the cert and private key, copy it to a location on the server you wish to monitor in the untrusted domain
3. On the server you wish to monitor, import the corresponding cert (created specifically for this machine) into the local machine’s personal store
Install the OpsMgr Agent and Associate Cert
1. On the machine in the untrusted domain, run the momagent.msi to install the agent manually
- Enter the management group name from the Management Server (name found in the registry under HKLM\SOFTWARE\Microsoft\Microsoft Operations Manager\3.0\Server Management Groups)
- Enter any action account you wish (we created one in the untrusted domain and added it to the Run As accounts in the Management Server, then to the Privileged Monitoring Account Run As Profile)
- From an elevated command prompt, run momcertimport.exe and select the certificate that was just imported
Approve the Client
1. Unless you have automatic approval on for manually installed agents, you will have to approve the client in the Pending Management portion of the Administration section