Knowing where users login, and when, can be a very useful tool, especially when it comes to an organization’s cybersecurity efforts. For example, you could potentially spot when a user account has been compromised, or when a user has a pattern of usage that looks highly irregular. Fortunately, the information you would need to do this is available through Active Directory. Unfortunately, it might not be obvious how to extract that useful information and look for patterns.
Here, I outline an easy way to configure Active Directory to track the last five computers a user has logged into, and store that information in Active Directory for later reporting. This will allow you and your team to more easily track users and look for patterns—for example, if a user that almost always logs in from one location is also periodically logging in from another distant location, it could be a sign that they gave their credentials to someone else in another office. That would be worth a follow-up.
If you are on an IT team and this sounds like something you want to do, I recommend skipping to the “how to” below. If you are new to Active Directory, I recommend reading this 10-second overview:
What is Active Directory, and Why Use It to Track Where Users Log In?
First, what is Active Directory? Active Directory is a directory service that can be run on a Windows server. That server (called a domain controller) is used to authenticate and authorize all users seeking access to a Windows domain network.
One the one hand, this gives users flexibility, as they can access other computers on the network that they have permission to access. This is possible because all IP addresses, computer names, and users are stored in a central “catalog,” removing the need to have different logins for all machines.
On the other hand, it gives administrators more information and control, because they can oversee everything that happens within their domain. For example, they can see who is logging in, and from where. They can also prevent a user from logging on—useful, for example, if you need to run an audit.
Using the Active Directory Comment Field for Tracking
To track multiple logins, we will need to use a multivalued field. A multivalue attribute can contain multiple values, all of uniform syntax.
(Note that multivalue attributes hold a set of values with no particular order. There is no guarantee that multivalue properties are ever going to be returned in the order in which they were stored, or any other order. There are ways to fix the order, though.)
For our purposes here, the comment field will do nicely. We’ll have to use a script to write the necessary information; fortunately, I’ve provided one in the step-by-step below.
Step-by-Step Guide to Setting Up Active Directory to Track Where Users Log In
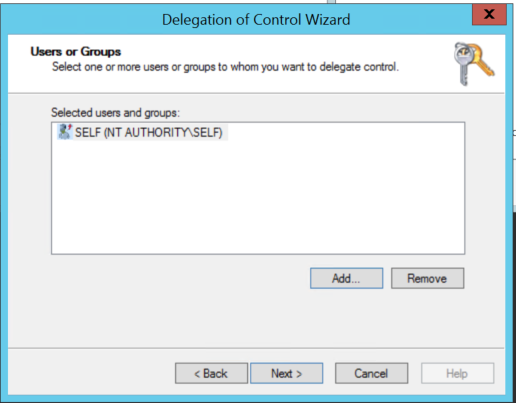
Step #1: In Active Directory, right-click your Domain (or OU containing the users you want to update) and select Delegate Control. Add the SELF account, then click Next.
Step #2: Select “Create a custom task to delegate”. Then select “Only the following objects in the folder” and check “User objects”. Next.

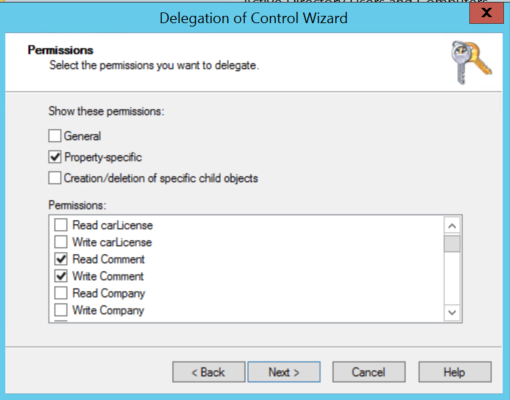
Step #3: Check “Property-specific” and then check “Read Comment and Write Comment”. Next.
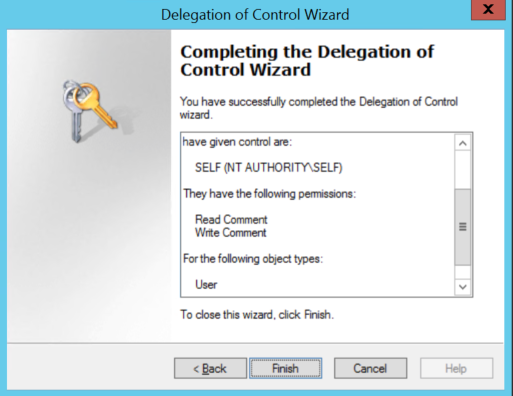
Step #4: The following script could be deployed using a Group Policy that will apply to users and add as a Login Script: User-comment-login
Step #5: You can now use Active Directory Users and Computers to search for a user account and see which computers they last logged onto, up to the last 5 logins.
You can also do a search using the comment field for *COMPUTERNAME* to find the user that last logged onto a specific computer.
What About Third-Party Products to Do This?
A handful of companies offer products to monitor users in one way or another. Many of them go to great lengths to argue that using their product is better than using Active Directory directly.
I won’t comment on specific products here. Some may well be useful. But, to me, it can be much more cost effective to set up Active Directory (and your reporting) to suit your specific needs. In fact, this can be just one of several automations you can use for better cybersecurity across the organization.
If that sounds appealing to you and your team, please reach out. We would love to discuss further.