Microsoft Ignite 2021 Microsoft held their annual Ignite conference at the beginning of November, announcing a slew of new features, functionality,...


Microsoft Ignite 2021 Microsoft held their annual Ignite conference at the beginning of November, announcing a slew of new features, functionality,...

Inefficient app deployment is one of the big causes of resource waste (and endpoint security holes) that we address here at Model Technology...

Hi everyone. Welcome. My name is Jason Rutherford and I'm the Managing Partner for Model Technology Solutions. Today I'm going to show you...
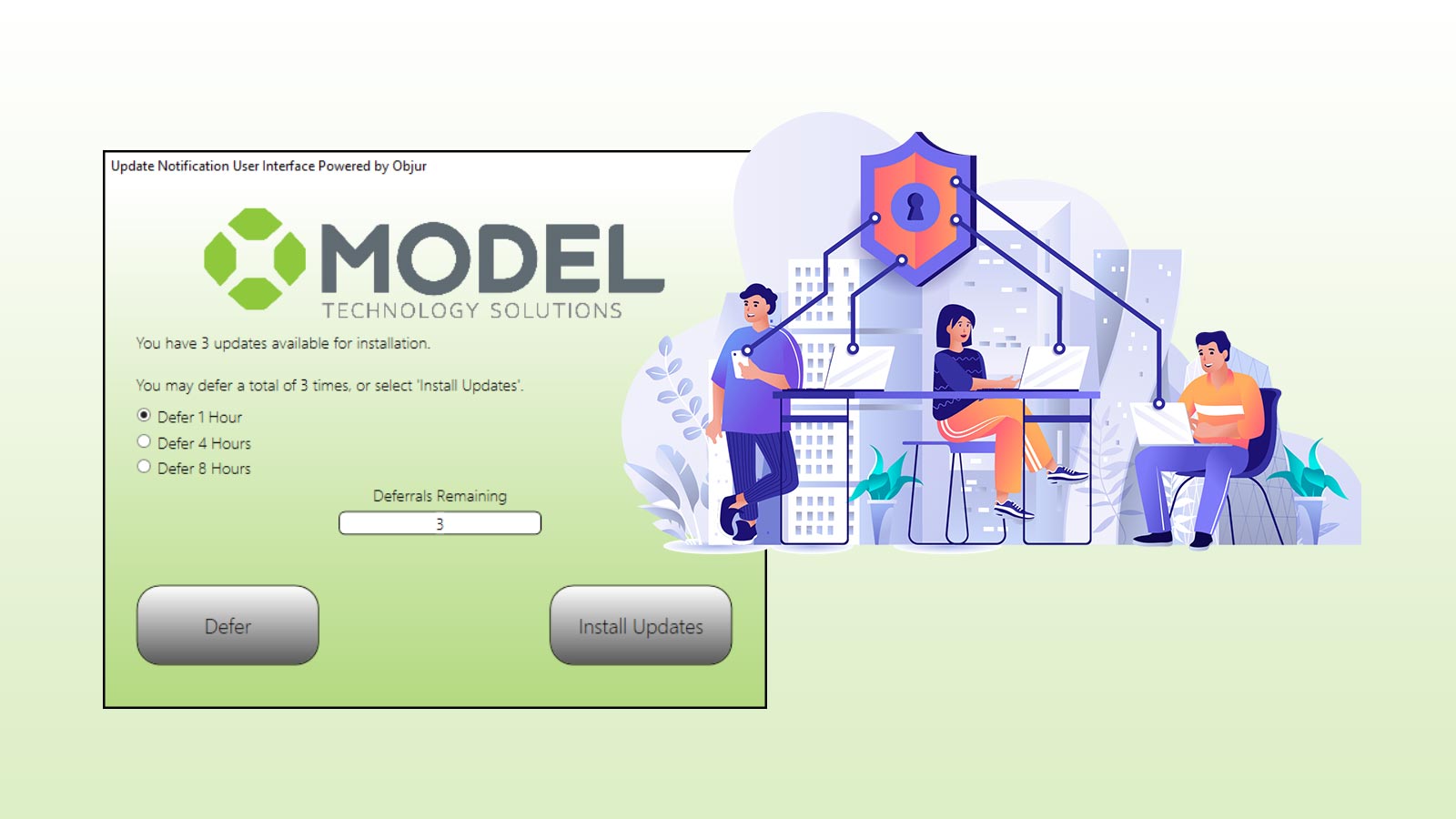
It's all about the boot, not just the patch. Endpoint patching only increases security when the end user reboots and applies the update to their...
![It Really Works! How To Do More With The Same Resources in Multiple Industries Through UEM [Case Studies]](https://b2186977.smushcdn.com/2186977/wp-content/uploads/2021/08/Featured-Image-Template.jpg?lossy=0&strip=0&webp=1)
You might be wondering, "What is Unified Endpoint Management?" The common definition of UEM is a single platform for management of devices such as...
In today’s hyper-connected digital landscape, system compromise remains one of the most pressing...
In an era where cyber threats evolve faster than many organizations can respond, situational...
In today’s digital-first business environment, companies rely on third-party vendors and service...
Prove you’re cyber-ready and reduce your premiums through our NIST-based cybersecurity assessment. Then make the most of your assessment results through monthly consulting sessions with our vCISO Director of Cybersecurity.