This post is part of a multi-part series defining maturity model levels for endpoint devices. Today we will be covering Endpoint Security Level 5. In this post you’ll read about:
- What is Unified Endpoint Management (UEM)?
- Our proprietary maturity model, its phases and categories.
- An overview of security level 5 within the maturity model.
To access the previous Level 4 Endpoint security, you can read the post here.
But before we jump into Level 5, let’s start with an overview of our UEM Maturity Model.
Our Proprietary Maturity Model
Our UEM Maturity Model was developed to help customers:
- Initially assess their infrastructure’s maturity.
- Compare their infrastructure maturity relative to other organizations.
- Confirm that they are on the right path to higher maturity.
- Help define what that the “right path to higher maturity” looks like in the first place.
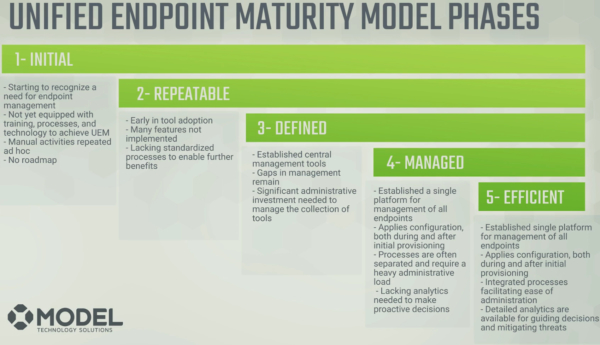
These are the phases of our maturity model. Generally speaking, these phases are common in the industry. They include the:
- Initial phase: You’re starting to realize something is needed.
- Repeatable phase: You’re able to get some things accomplished, but you’re lacking standardization from a high level.
- Defined phase: You’ve got more central management tools, but there may be some gaps in management.
- Managed phase: You start feeling like what we’re going call a well oiled machine. You’re applying configuration pre and post, and processes are there but they sometimes require more heavy touch than what you’d like.
- Efficient phase: You’ve got a single platform for all of your endpoints, you’re applying configuration dynamically, and you’ve got a set of analytics that are driving decisions.
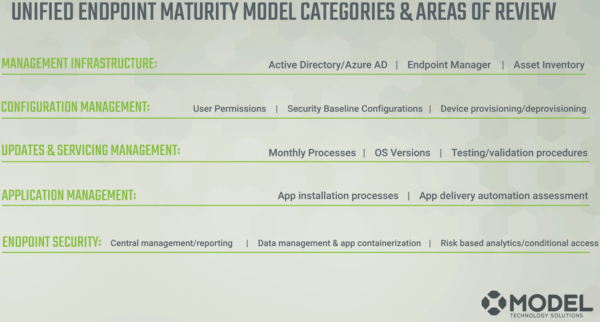
Those phases we then apply to the proprietary categories of our maturity model. These categories include:
- Endpoint Arena: Management infrastructure, active directory, and Azure AD endpoint manager.
- Configuration Management: User permissions, security baselines, device provisioning, and deprovisioning.
- Updates and Servicing Management Arena: Monthly processes, operating system versions, testing and validation procedures.
- Application Management: How applications get installed, what that process looks like from an organization level, and how those apps are delivered.
- Endpoint Security: Where you’re at today, how you manage, how you report on security, what the data is doing, app containerization, risk based analysis and conditional access.
But what’s the purpose of this maturity model? What can it do for you, and how do we use it for our customers?
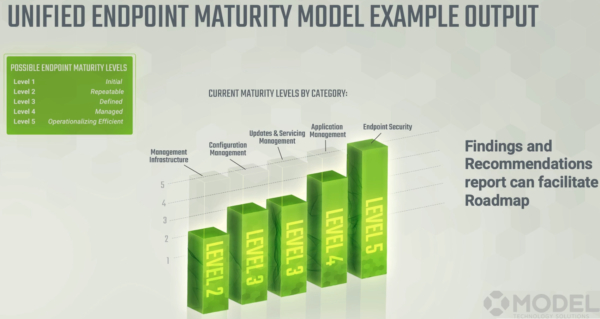
Our maturity model helps you graphically define where you sit in a categoric view based on the phases. For example, maybe your management infrastructure is a level two like the graphic below. That’s an area that could easily be brought up to a three to bring it up to par with everything else. The maturity model would show you that and then help you to identify the best areas to improve to bring it up to par.
Level 5 Endpoint Security
In today’s post we’re covering Level 5 Endpoint Security. To read about the previous level, Level 4 Managed, you can visit this post here.
What does Level 5 efficient look like? Similarly to level 4, in a level 5 you have:
- Centralized tools
- Application level management
- Multifactor authentication
But when you get to the Level 5, a couple other things get added to the mix:
- Just in time access configuration
- Centralized analytics.
Just In Time Administration
Just In Time Administration is being able to manage technicians that have the ability to change your environment and not giving their credentials out on a regular basis.
For example, let’s say that you have an administrator and that wants to go manage Azure Active Directory. With Just In Time Administration, they cannot do that without requesting access first.
You can certainly automate approvals of the activation of permissions, but adding the extra step of needing to request those permissions before you can execute anything has the ability to thwart some serious attacks on your infrastructure.
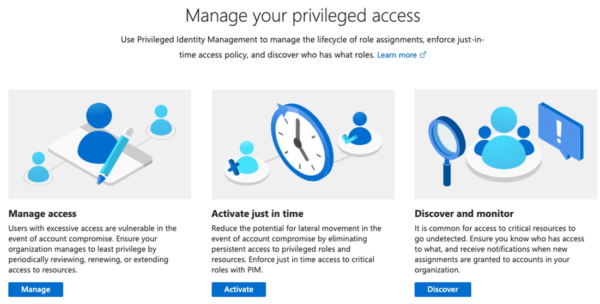
Privileged Identity Management
Using something like Privileged Identity Management (PIM) inside of Azure Active Directory:
- Allows you to set and configure access for a variety of different roles
- Gives you discovery and monitoring capabilities
- Allows you to activate that just in time feature
Centralized Analytics
Another element provided by Level 4 and particularly Level 5 are centralized analytics. Having centralized analytics is helpful because you can see what applications are being used in your organization and what applications are accessing what kind of data. The analytics provided by Cloud App Discovery are a good example.
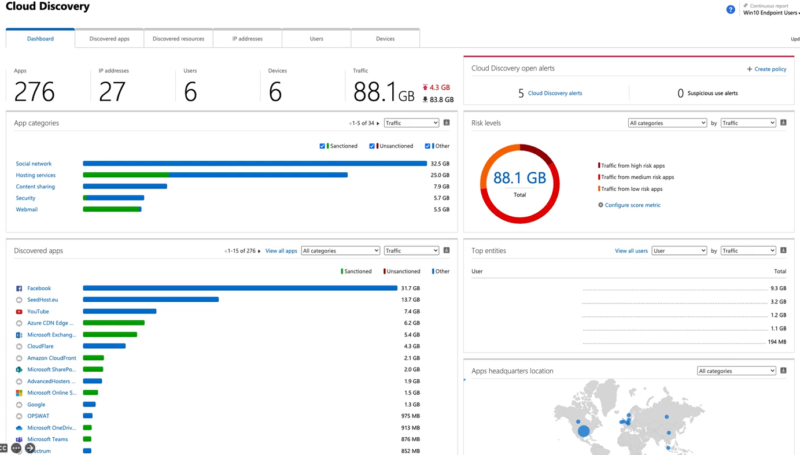
Again, in Defender 365, you can look at:
- Your different users
- Their compliance
- How their compliance looks on a scoring chart, using something like Model Technology’s secure score to define how secure your organization is overall across many platforms
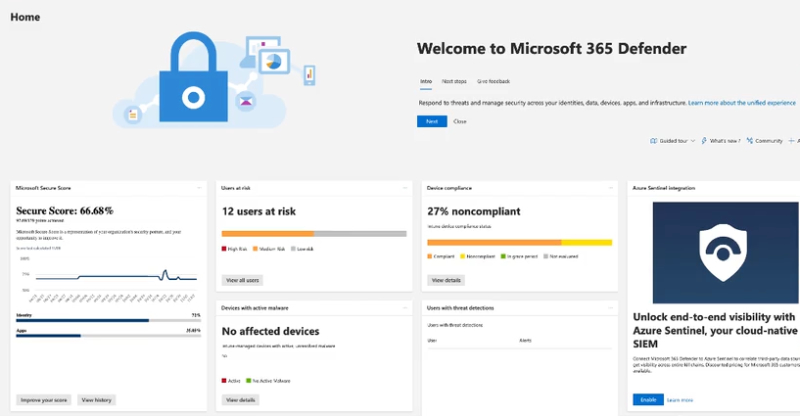
Defender for Cloud is another example. It provides a lot of insights into:
- Regulatory compliance
- Azure Virtual Machines
- Information protection
- And more.
You can see that all of this data can be accessed by locking down the various aspects of your cloud footprint in a modern world.
Single Source Analytics
At Level 5 Endpoint Security, single source infrastructure analytics are available as well. What that means is you’re taking that data from the Level 4 and asking how it makes sense to your administrators. How can it be aggregated into small, easily digestible chunks instead of one massive pile of data?
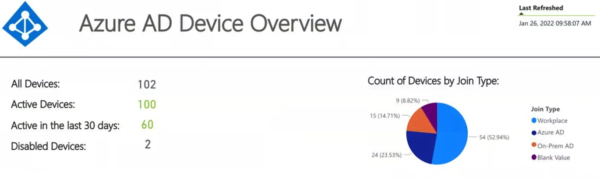
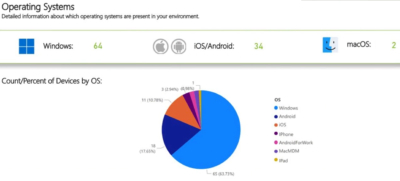
As an example, the Azure Active Directory plugin that aggregates data from Azure Active Directory gives you some high level analytics and searching capabilities for
- Devices
- Device types
- Versioning
- And more
That allows you to really start getting a handle on managing your Azure Active Directory more proactively!
Intune also has some reporting included. However, there’s a lot to be desired in how you navigate and find actual data you’re need within the reports. For a comprehensive look at accessing data from Microsoft Intune, you can read our three-part series on this subject starting here.
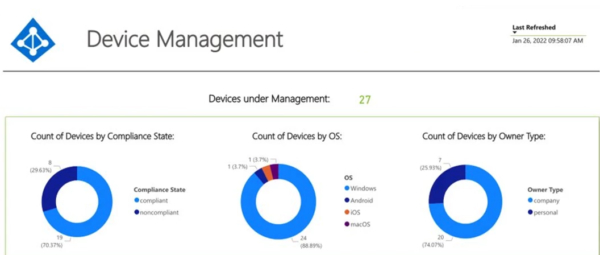
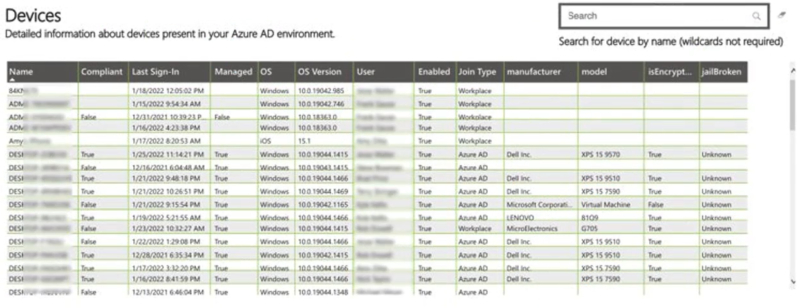
Single Source Analytics also allow you to look not only at how the devices are joined and if they’re compliant but also quickly identify why they’re not compliant. If you’ve ever tried to do this inside of Intune, you know that it can be a challenge to quickly determine on a mass scale why machines are not compliant. But with Level 5, this kind of query is possible.
Why is that important? With Endpoint Security, you want to be as proactive as possible…or at least reduce the amount of time to reactivity by leveraging analytics to drive these business decisions. You don’t want to be firing in the dark with the actions that you take. You need data, and Single Source Analytics gives you an easy way to translate the data that you’re gathering in Level 4 into actionable visuals presenting them.
For example, the dashboards in Defender for Endpoint tell you:
- How many devices are in Defender for Endpoint
- How many are present in Active Directory
- How many are not present in Active Directory
- The active devices by operating system count
- How many are onboarded
- How many are being managed by Intune
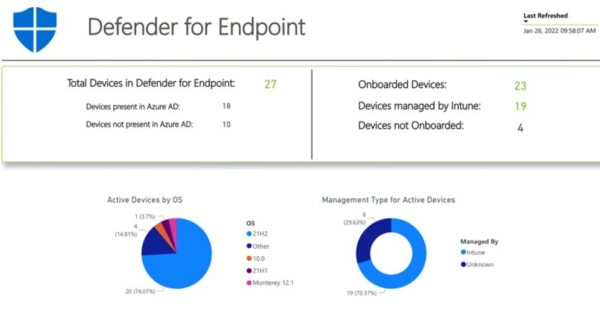
This is difficult information to discern from those dashboards, but it’s instrumental for proactively managing your environment. Being able to quickly identify which devices have vulnerabilities by any search criteria possible is huge. Defender gives you these kinds of criteria:
- Computer name
- Username
- Severity
- Exposure
- Onboarding status of Defender
- Last activity
- Relevant dates
Being able to sort by this information is very important to help you identify updates required in your organization.
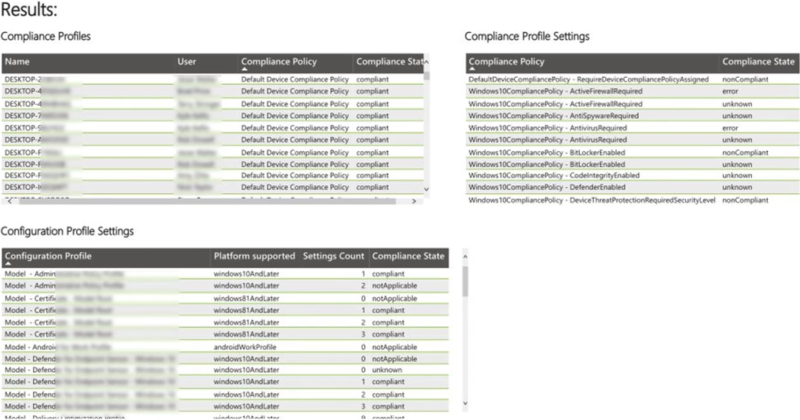
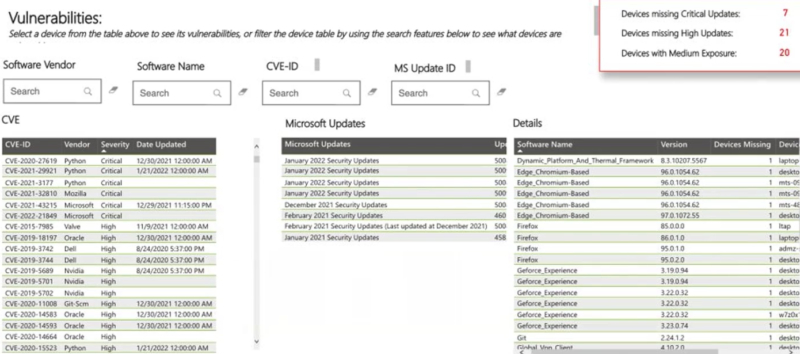
In the below Defender for Endpoint screenshot, you can see:
- The CVE ID matched to the Microsoft updates
- The details of the software that has the exposure
- A summary of devices missing critical updates, high priority updates, and/or medium priority updates

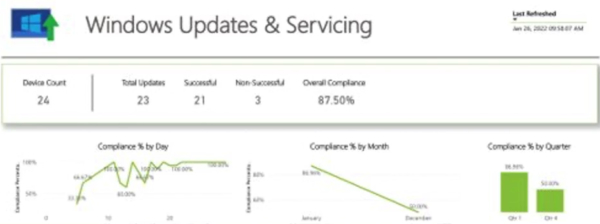
The last dashboard is the Windows Updates and Servicing. This allows you to see an over-time view of compliance history based on the Intune patches being pushed out with Windows Update for Business.




The Maturity Model Analysis
Now, you might be thinking, a lot of this data is very difficult to find and quickly make sense of. Where do I go from here?
We’d love to help you answer this question by through our Maturity Model Assessment. This assessment will help you to:
- Benchmark your infrastructure maturity
- Identify steps to close the gaps you think need to be closed
- Know exactly how you could improve your compliance, security, and efficiency, and cut costs while you do
- Confirm your technical direction
- Ensure your strategy is aligned with a Microsoft modern managed approach
This information is hugely valuable for a modern endpoint management and ensuring your endpoints are as secure and your operation as efficient as is possible with all the complexities of doing endpoint management today.
Practically, this assessment consists of two 90 minute sessions. From those sessions, we’ll deliver you a Findings and Recommendations Document that will help you to understand how to get from your current maturity to the more-mature levels and reap the benefits thereof.
If you’d like to know more about the maturity assessment, just head to this webpage and download the questionnaire. Or if you have any questions, please don’t hesitate to reach out. I can be found at jason.ruthford.model-technology.com.
