My name is Jason Rutherford, and I’m the Managing Partner of Model Technology Solutions. The last two years have shifted the landscape of Endpoint Security. Gone are the days when caring about cybersecurity was relegated to a small group of techies behind the scenes at the largest companies. COVID 19 and other factors have quickly moved a large portion of our workplace into remote work, and cybercrime has become a forefront issue for both our nation’s decisionmakers and many average American families. These days everyone from your average worker who uses online banking to the most-powerful CEO has in the back of their mind the possibility of being affected by criminals who use the internet as their means.
Adaptability triumphs over strength, and as things change so must our mindset. And in this post I’m going to discuss one of the biggest mindset shifts that you can make to walk the path of improving your endpoint security: Shifting to a single-platform security solution, particularly Microsoft. Specifically I’m going to discuss:
-
- Security and what it looks like today
- Gartner’s take on security trends
- Microsoft as a Leader in integrated security within organizations
- How Model can help enhance your security
What Does Endpoint Security Mean Today?
Let’s begin by talking about security. What exactly are you securing? Some of the things that need to be secured in an organization are:
- Data: At rest, in transit, and through a variety of scenarios, such as on a corporate device or a personal device or a mobile device.
- Identities: By using intelligent and risk-based analysis. As an example, a user logs in, and then if the user suddenly logs in again from another country. That kind of activity should be automatically identified.
- Endpoints: Corporate or personal, defining what the minimum state required to access resources from a compliance purview would look like.
- Applications: The vehicle in which you access application data. Whether they’re on-prem or SaaS applications, they need to be secured.
- Infrastructure: By establishing rules around when your administrators can access and administer the infrastructure.
- Network: Whether public or private, you’re making sure it’s properly segmented.
These are the elements that are involved in identifying and talking about security.
Ideally, the security of all these elements are integrated using a single tool for a complete view of your digital estate. In the best case scenario, whatever tool you use has analytics and allows for automated responses to increase your security posture as an organization. Ultimately, you want a single tool (or seamlessly integrated set of tools) to handle your security needs that allows for all the functionality that you want.
Gartner’s 2021 Security and Risk Trends
In 2021, Gartner defined some security and risk trends.
- Vendor consolidation: 75% of CISOs have more than 16 tools all managing security. This is far too many, as having too many tools increases redundancy and cost.
- Identity first: Misused credentials are the top technique used in breaches.
- Managing machine identities: Secrets and certificates are becoming more important these days, so companies need to develop an enterprise strategy for machine identity.
- Remote work: This is going to be a reality for work moving forward. Users need to access their data, apps, and support which they used to have access to in person when they were on-prem.
This is where that mindset shift comes in. Security is not what it once was. Modern security needs to enable the world’s new work methods and centralize tools as much as possible to remove inefficiency, cut costs, and ultimately make life easier for your IT team. This is why we think that today, when you think of integrated security and security leaders in business environments, Microsoft’s security suite should be top of your list.
Microsoft: A Leader in Gartner’s 2021 Magic Quadrants
If you take a look at the 2021 Magic Quadrant for Access Management, Microsoft is named the leader.
If we take a look at the Unified Endpoint Management tools in 2021, Microsoft’s the leader, again, only slightly behind VMWare in completeness of vision, and well beyond them in ability to implement.
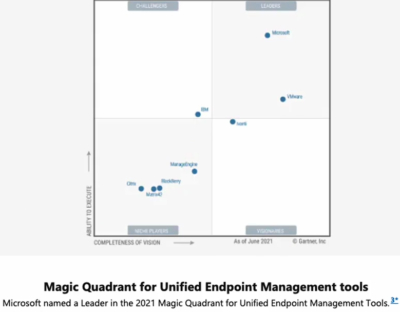
This was not the case back in 2016, 2017 related to Enterprise Information Archiving. Microsoft was then only one contender in a close pack of leaders.
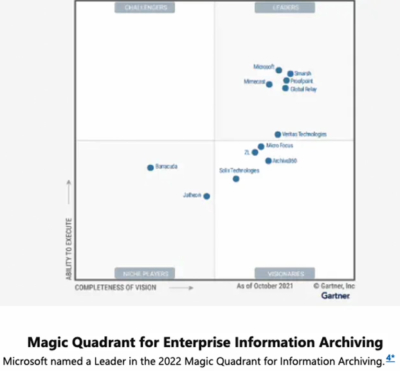
However, over the years, their focus has shifted to becoming a leader in Enterprise Information Archiving and Endpoint Protection Platforms, quickly rising to the top.
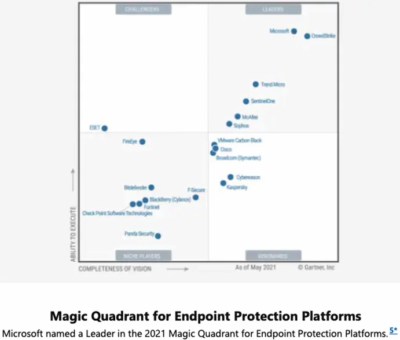
This is a pattern that has occurred over time, again and again, from the SMS and SCCM configuration management days to where they currently sit. This pattern has left Microsoft a leader in Endpoint security with a defined their Zero-Trust infrastructure.
Their motto? “Never trust, and always verify.”
So, how does this robust philosophy look practically? Well, some practical examples of security features that Microsoft offers are:
- Identities, both human and non-human
- Strong authentication
- Request enhancement
- Risk assessment of the authentication or forcing in some cases another enhancement in their authentication because the risk was assessed to be great
- Device management, corporate and personal
- Device compliance, which might change how the data gets accessed
- Ability to classify, label, and encrypt data
- Different application levels of access at different time through technologies like PIM
And these features are just scratching the surface. Ultimately, what all of this means is that you should strongly consider Microsoft as a top pick for your consolidated vendor toolset moving into 2022.
Model Helps Companies Fully Implement The Microsoft Suite
So, let’s say you’re considering Microsoft for your security needs. What’s next? This is where we can help.
We’ll Assess Your Infrastructure
Your first step is to assess your organization’s maturity related to Zero-Trust security. We provide a Maturity Health Check Service that can help you benchmark your IT maturity, including your endpoint security.
We’ve created a proprietary maturity model related to Unified Endpoint Management. The maturity model includes five categories and five phases for each category.
The categories are:
- Management infrastructure
- Configuration management
- Updates and servicing
- Applications
- Endpoint security
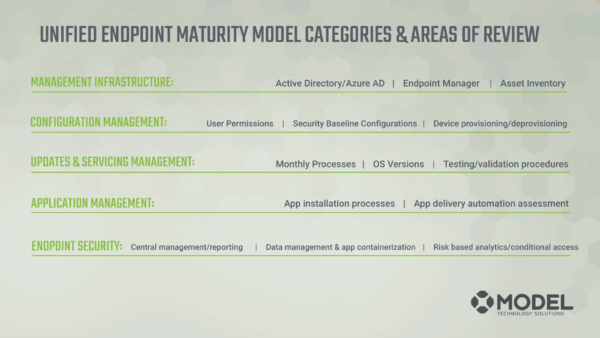
From least- to most-mature, the phases are:
- Initial
- Repeatable
- Defined
- Managed
- Efficient
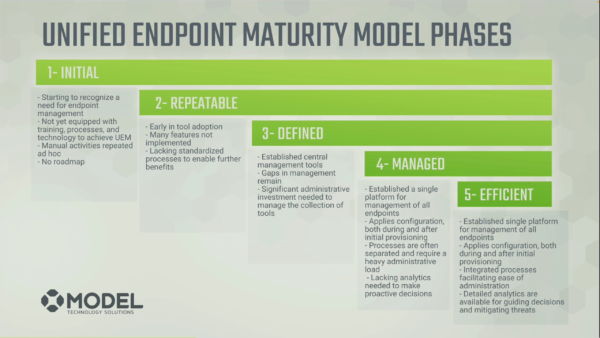
Based on this maturity model, we assess your organization’s maturity in each category – including Endpoint Security – from one to five. After doing so, we provide a report in this so that you can take actionable steps to improve your Unified Endpoint Management and security through effective and cost-efficient projects.
We’ll Help You Implement Endpoint Security Projects
Depending on your need specifically, we can also directly address your projects from two perspectives:
Consulting
We provide single-project consulting and implementation work for companies wanting help. This is a temporary partnership where provide our expertise, our knowledge, work alongside your team to transfer that knowledge, and then go away. To learn more about this service, visit our consulting services page.
Managed Services
We also partner with companies to manage security tasks, freeing them up for other value-added projects. This is a longer-term partnership where we become an extension of your team by providing more hands, SLAs, and helping you meet objectives.
This is our ServiceNow portal used by our Managed Services team. It includes types of requests that we can help handle for your organization.
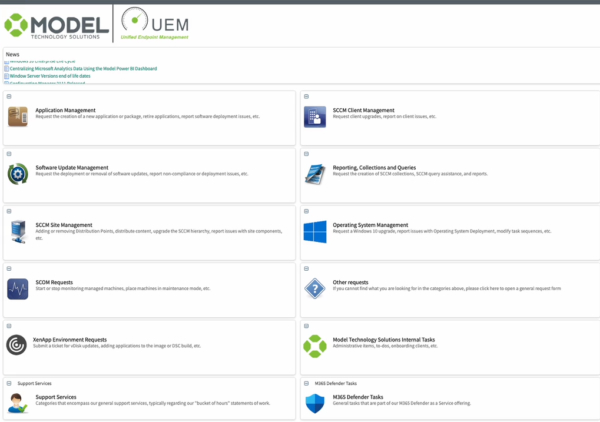
To learn more about this service, you can visit our managed services page.
We’ll Help Improve Your Analytics and Reporting Capabilities
We can also help improve reporting from the Microsoft Suite. The Microsoft suite is robust in many ways, though one of the areas it still struggles is in analytics and reporting. To fill this gap, we’ve created a custom dashboard built in Power BI that leverages Graph API, Azure API data, and the Microsoft Security Center data or M365 Defender for devices data and displays them in a convenient real-time interface. Ultimately, the security pane of the dashboard takes all this complex security information and consolidates it down to:
- Percentage risk to the organization
- Number of exposures
- Number of devices that are impacted
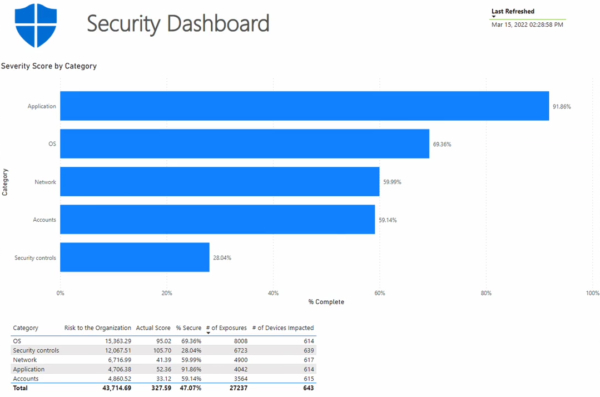
Having this information enables agile security monitoring and easy access of security information in real-time rather than digging through the individual software and aggregating complex data by hand. To learn more about this dashboard, you can watch a demo here.
Next Steps To Change Your Mindset
Like I said earlier, as the world changes, so our mindsets must as well. We’d love to help you practically shift into the new era of remote-work and centralized Endpoint Security. Some basic next-steps for this would be:
- Consider consolidating security vendors if you’re looking at protecting data including identities, endpoints, applications, infrastructure, and network.
- Read the the Microsoft Zero Trust white paper. Even if Zero Trust isn’t what you think about when talking about security and securing your organization, this is a powerful piece that will likely influence your security mindset.
- Learn more about (and possibly invest in) the Microsoft toolset including Defender for Cloud apps, Defender for Identity, Defender for Endpoint, Compliance Center, Endpoint Manager, and Privilege Identity Manager. These are a powerful set of tools, so much so we’ve dedicated our professional careers to helping companies to implement them to the greatest degree possible for the greatest possible security.
We’d love to help you practically to take these steps. Feel free to reach out via our contact-us page, or you can also email me directly at Jason.Rutherford@model-technology.com. I’d love to hear from you.

